Keys Findings
World Leaksemerged in early 2025 as a new project by the operators of the Hunters International ransomware group, shifting from double extortion with ransomware to extortion-only attacks due to increased risks and reduced profitability.- The
World Leaksand Hunters International platforms share numerous similarities in design, layout, and functionality. World Leaksoperates four distinct platforms: a main data leak site, a negotiation site for ransom payments, an Insider platform for journalists, and an affiliate panel.World Leaksfaced initial bugs, downtime, and fluctuations in claimed data leak sizes, raising questions about data accuracy.- Despite claiming to be extortion-only, some victims suffered ransomware deployment.
- We learned that the
Secp0ransomware group is collaborating withWorld Leaks, indicating potential future attractiveness for other threat actors.
Executive Summary
World Leaks, a new extortion platform, emerged in early 2025 as a project by the operators of the Hunters International ransomware group. This shift from double extortion with ransomware to extortion-only attacks was driven by increased risks and reduced profitability in the ransomware ecosystem. The platform shares numerous similarities with Hunters International in design, layout, and functionality, and operates four distinct platforms: a main data leak site, a negotiation site for ransom payments, an Insider platform for journalists, and an affiliate panel. World Leaks faced initial challenges, including bugs, downtime, and fluctuations in claimed data leak sizes, raising questions about data accuracy. Despite claiming to be an extortion-only platform, some victims suffered ransomware deployment. World Leaks is an Extortion-as-a-Service platform, providing affiliates with an exfiltration tool. Investigations revealed that the Secp0 ransomware group is collaborating with World Leaks, indicating potential future attractiveness for other threat actors. The platform's hazardous beginning and operational challenges will be crucial in determining its future prospects.
What is “World Leaks”?
World Leaks is an extortion platform that emerged in early 2025. On January 1, 2025, according to a report by Group-IB, who were the first to publicly discover this threat, the operators of the Hunters International ransomware group launched a new project called "World Leaks". Due to actions taken by the authorities against the ransomware ecosystem and the negative impact of the geopolitical context, they deemed this "business" too risky and unprofitable. The operators decided to shift from double extortion with ransomware deployment to extortion-only attacks. With their Extortion-as-a-Service platform, they appear to aim to collaborate with other threat actors, who will be affiliated.

As highlighted in Group-IB's report, Hunters International published an internal note to their partners in November 2024 announcing the end of the project. However, the group remains active. We can deduce that "World Leaks" is either a side project of the criminal organization or a backup plan. Since the note was released, there have been more than 70 claimed victims by Hunters International. The group is still active and shows no signs of retiring from the ransomware ecosystem. There are numerous similarities between the World Leaks platform and the Hunters International platform. For instance, both websites share the same design, with the logo positioned in the same location. The list of compromised entities follows the same format, including a variety of time zones and statistics about the number of visitors. Additionally, both platforms feature similar pages, such as those for companies and news announcements.
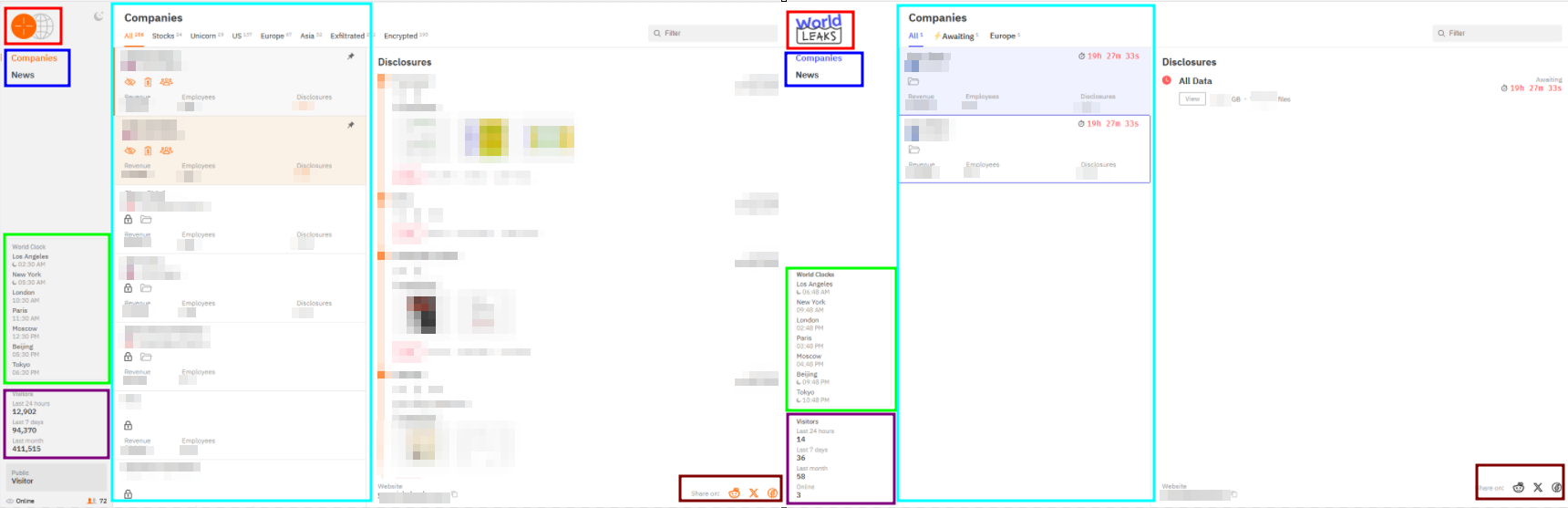
Even the file explorers used to search through the leaked data are alike. Both websites appear to use the same framework or assets, with only minor differences.
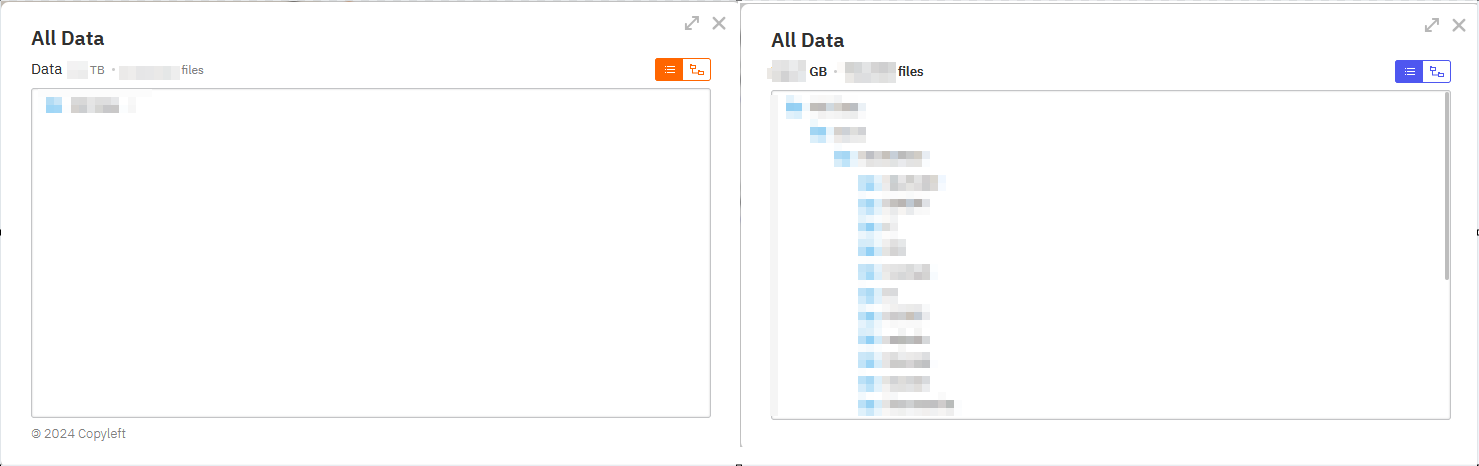
World Leaks’ different platforms
The operators behind World Leaks have developed four distinct platforms for their project. The first is their main data leak site, where they display their "trophy wall" showcasing all the victims' data that has been published or is scheduled for publication. The second platform is their negotiation site, which they provide to victims for the purpose of negotiating and facilitating ransom payments. Most recently, they have introduced their Insider platform, which is restricted to journalists and provides the press with 24-hour advance access to information about compromised victims. Lastly, there is their affiliate panel, which unfortunately we did not get access to.
World Leaks’ data leak site
Similar to Hunters International's data leak site, World Leaks' Data Leak Site (DLS) provides a list of claimed victims along with a timer indicating when the data will be released to the public. The website also features a News tab where the operators can publish information for the public.
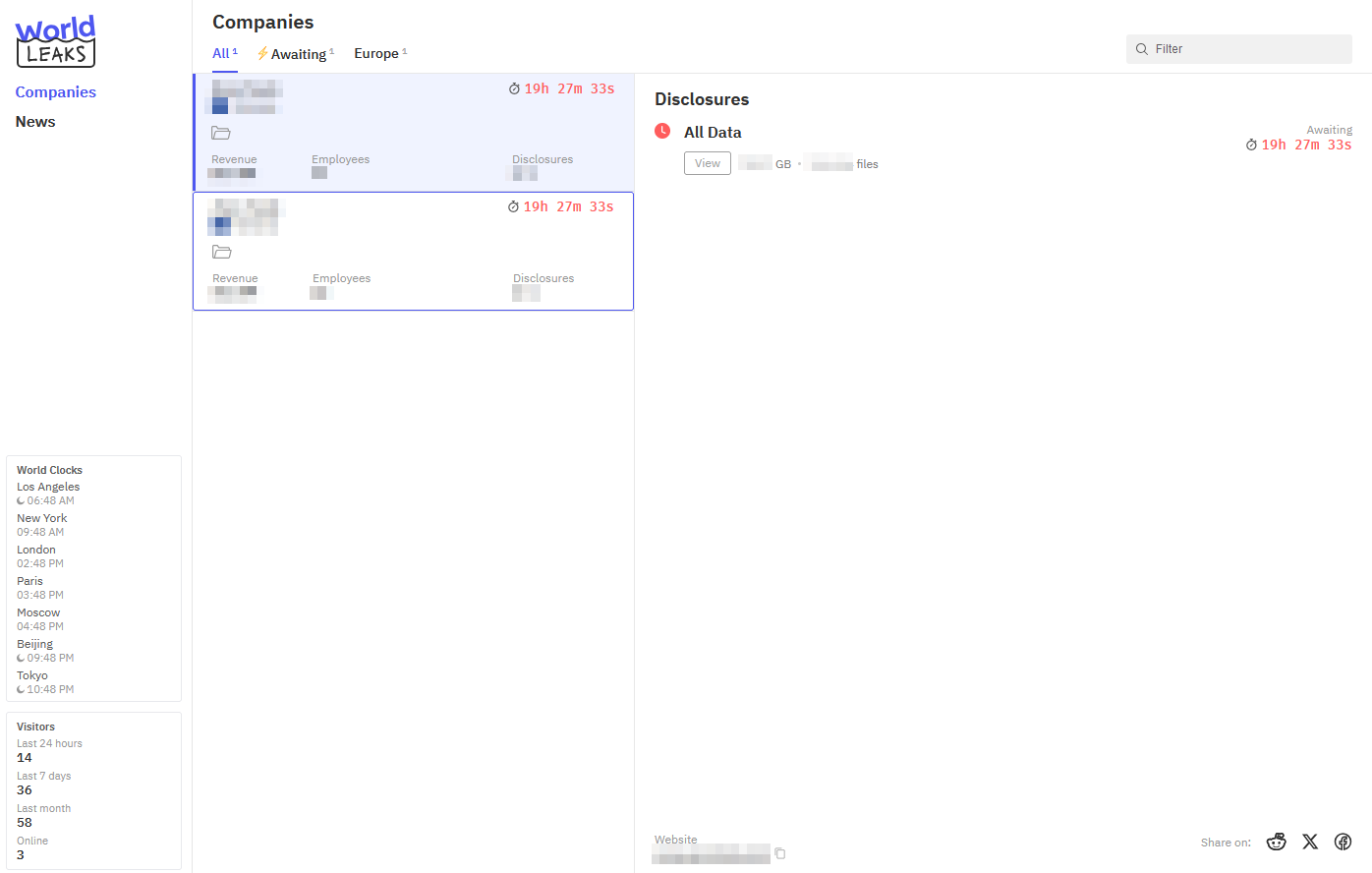
Recently, they added a "Sign Up" tab to allow journalists to register for access to the Insider platform.
As with their other projects, World Leaks offers the option to share information about compromised victims on social media platforms such as Reddit, Twitter/X, and Facebook.

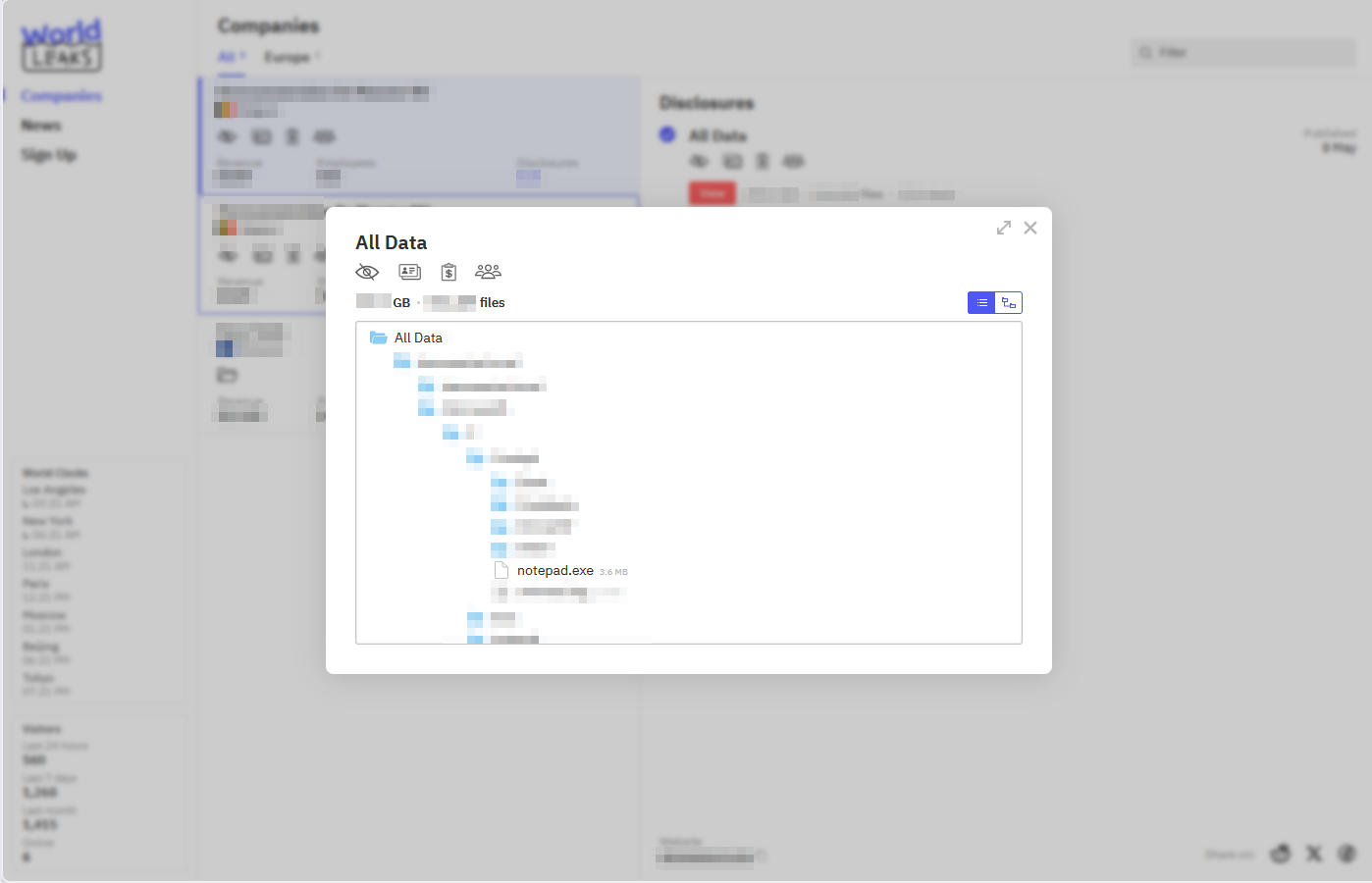
Additionally, like on their previous platform, their file explorer allows users to browse the list of leaked data and download specific files rather than downloading the entire data dump, which can be cumbersome when dealing with several terabytes of data.
World Leaks’ victim site
Similar to ransomware operations, World Leaks provides a victim panel for negotiation, payment, and for victims to view the data that has been exfiltrated by the threat actors. When claiming a compromise by e-mail, World Leaks provides the site address (in .onion) as well as a login and password to be used to access the panel.

Overall, the victim panel maintains a simple, mostly white and minimalistic design without elaborate styling, similar to the DLS site. This lack of visual complexity is intentional; each element is carefully crafted to maximize psychological pressure on the victim. From the countdown timer to the direct chat with threat actors and the storage page, every feature serves the single purpose of creating urgency, fear, and a sense of inevitability to coerce the victims into paying as quickly as possible.
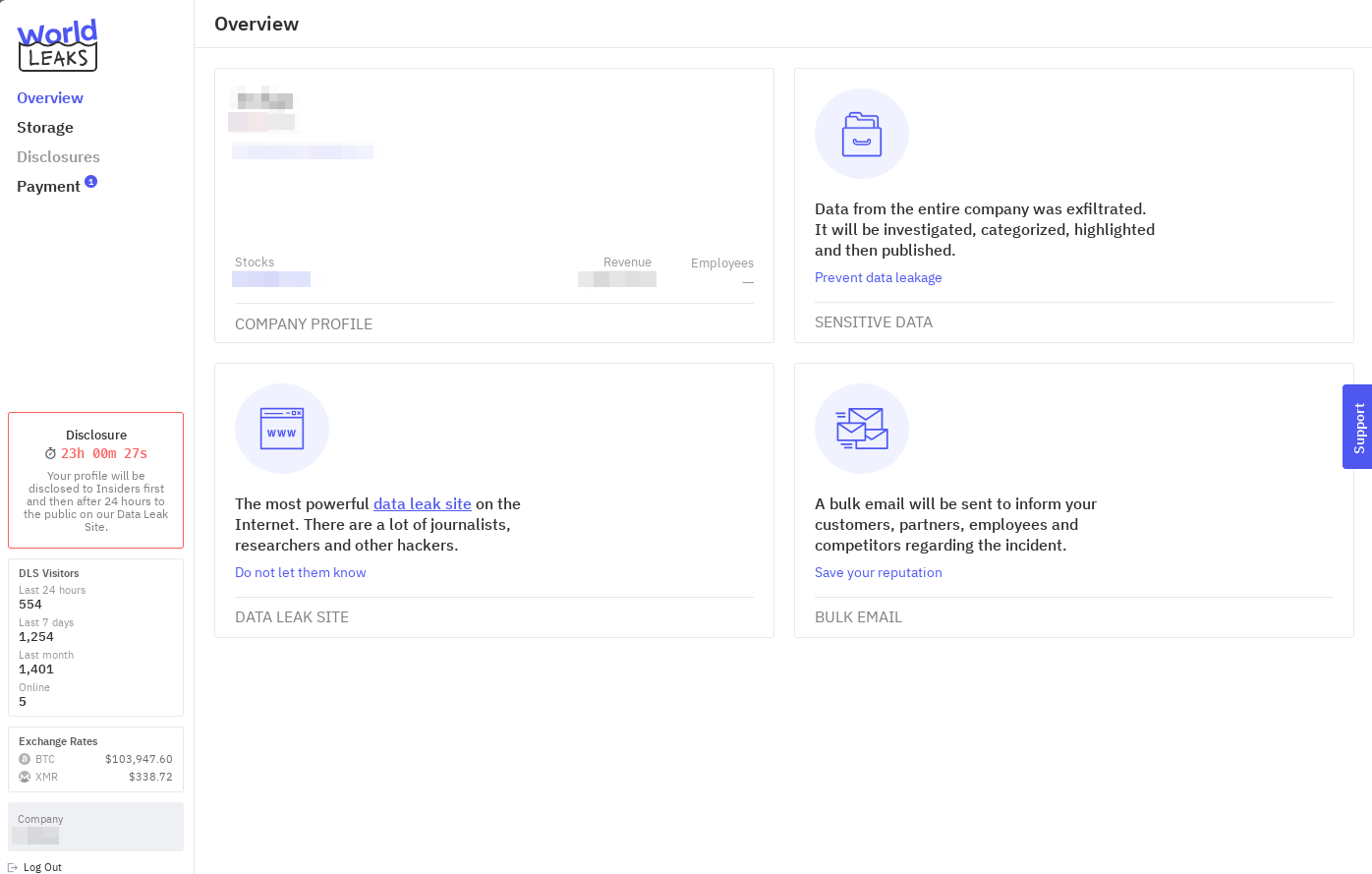
The interface offers various tabs. The Overview tab provides details about the victim, including the stock index, revenue, number of employees, name, and country. It also includes a link to their Data Leak Site (DLS) panel. The threat actors threaten to inform the victim's customers, partners, employees, and competitors about the incident if the ransom is not paid.
Additionally, there is a Storage tab where all the exfiltrated data is displayed in a file explorer similar to the one found in the DLS panel for claimed victims. Like the file explorer in the DLS panel, the interface mimics a typical file system structure, showing folders and files exfiltrated from compromised servers and user workstations. Victims can click through directories and open individual files, confirming the presence of confidential, internal, or sensitive data like financial records, employee documents, legal files, or customer information. This tab also features an "Erase" button, which is purportedly used to erase all the data once the ransom payment has been made. However, as is often the case, it is highly probable that not all the data will be erased even after payment, and the threat actors will still retain possession of sensitive information.
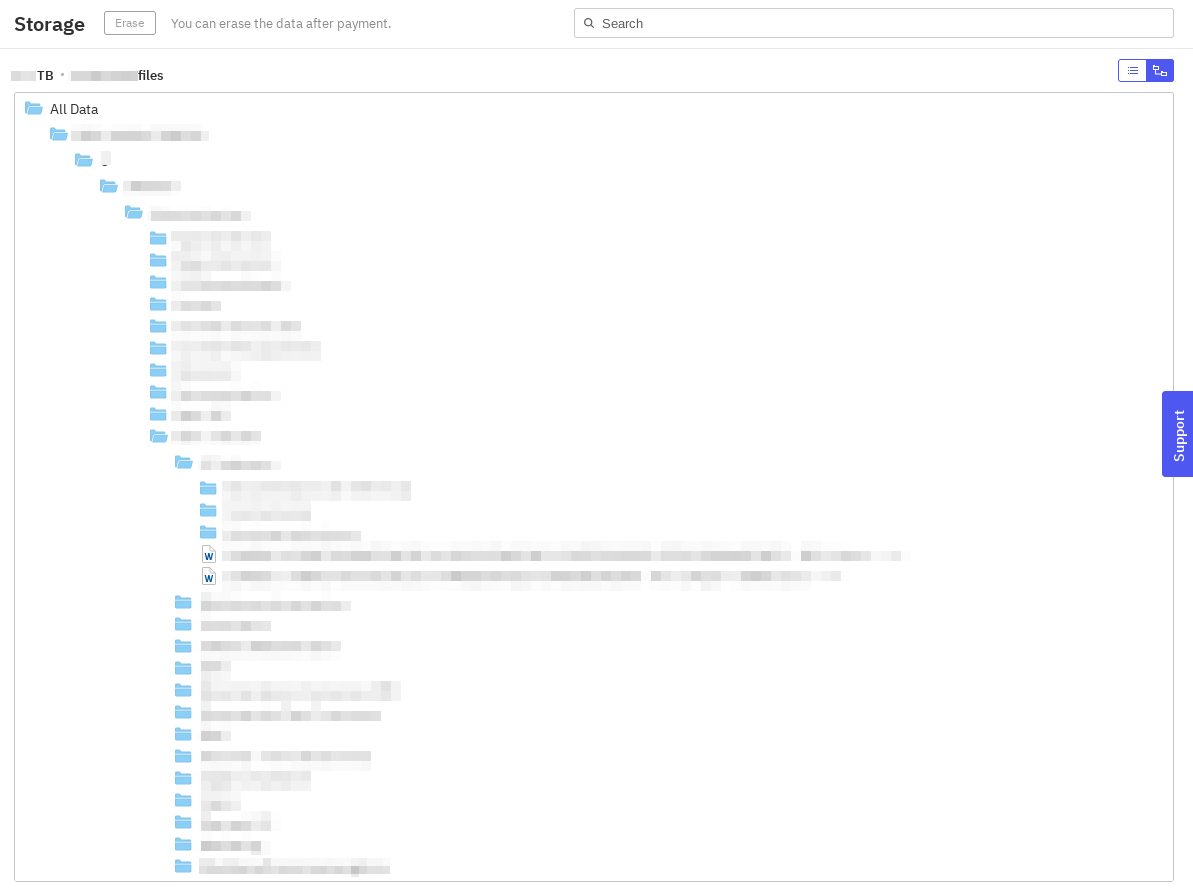
This setup serves two key functions:
- Validation: It provides tangible proof that the attackers have successfully exfiltrated internal data. For organizations still in doubt or assessing the extent of the breach, this can serve as a confirmation that the threat is real.
- Psychological leverage: By selectively exposing sensitive files, the attackers aim to escalate pressure on the victim, especially when high-impact documents are made accessible in clear form.
Importantly, this system bypasses the practical issues often associated with Tor downloads: slow speeds, broken transfers, and the need to retrieve large amounts of data just to verify the breach. Instead, everything is made instantly browsable, reinforcing the credibility of the attackers’ claims and making the extortion more convincing. The platform also features a "Disclosure" tab. Before the disclosure, the page does not yet contain any visible leaked data. Instead, a placeholder message reading “Disclosure data are preparing” is prominently displayed. This suggests that the attackers are either in the process of organizing or staging the exfiltrated data for public access, or they are deliberately delaying exposure as part of their extortion strategy.
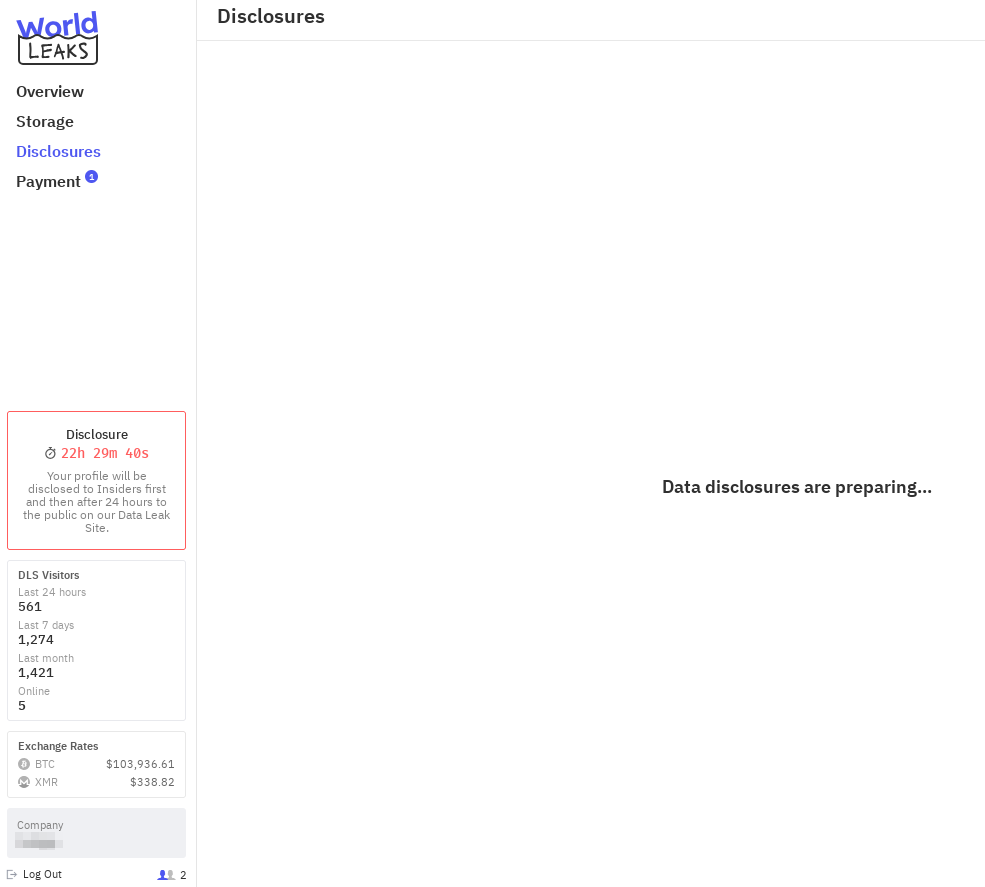
Obviously, the platform also includes a "Payment" tab. Payments are required to be made in Bitcoin to what appears to be a freshly generated address with no prior transactions. This practice is typical among ransomware operators, as it prevents linking payments to other campaigns or victims.
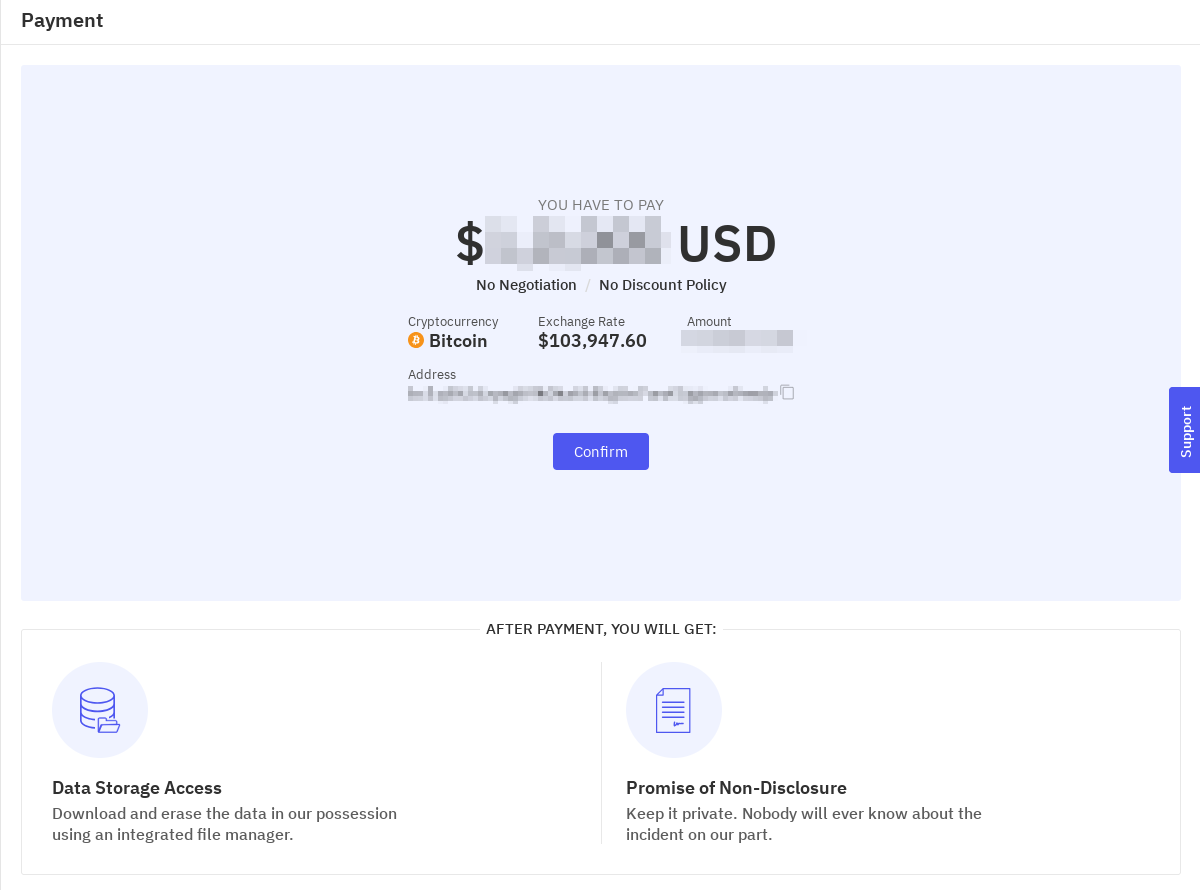
Once the payment is supposedly completed, the victim is instructed to click a “Confirm” button, which opens a confirmation popup. This popup includes a field where the user must input the Bitcoin transaction ID (TXID) corresponding to the ransom payment.
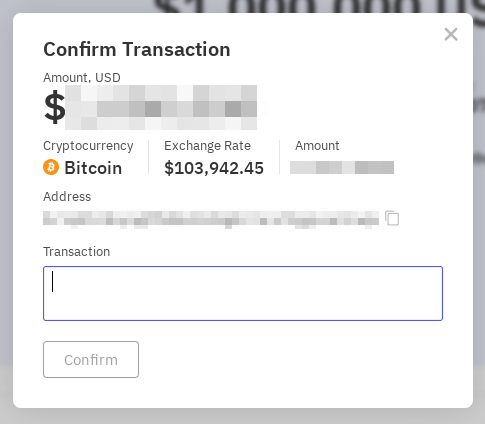
Despite the "Payment" tab displaying "No Negotiation" and "No Discount Policy," the platform offers a support chat where it is possible to communicate with the threat actors. On several occasions, the operators were observed initiating a conversation once they had detected a user online, using this as an opportunity to increase pressure. They warn that the leaked data will soon be made public if the ransom is not paid promptly. This interactive element not only reinforces the urgency but also serves as a psychological tool to intimidate victims and demonstrate the attackers’ control over the situation.
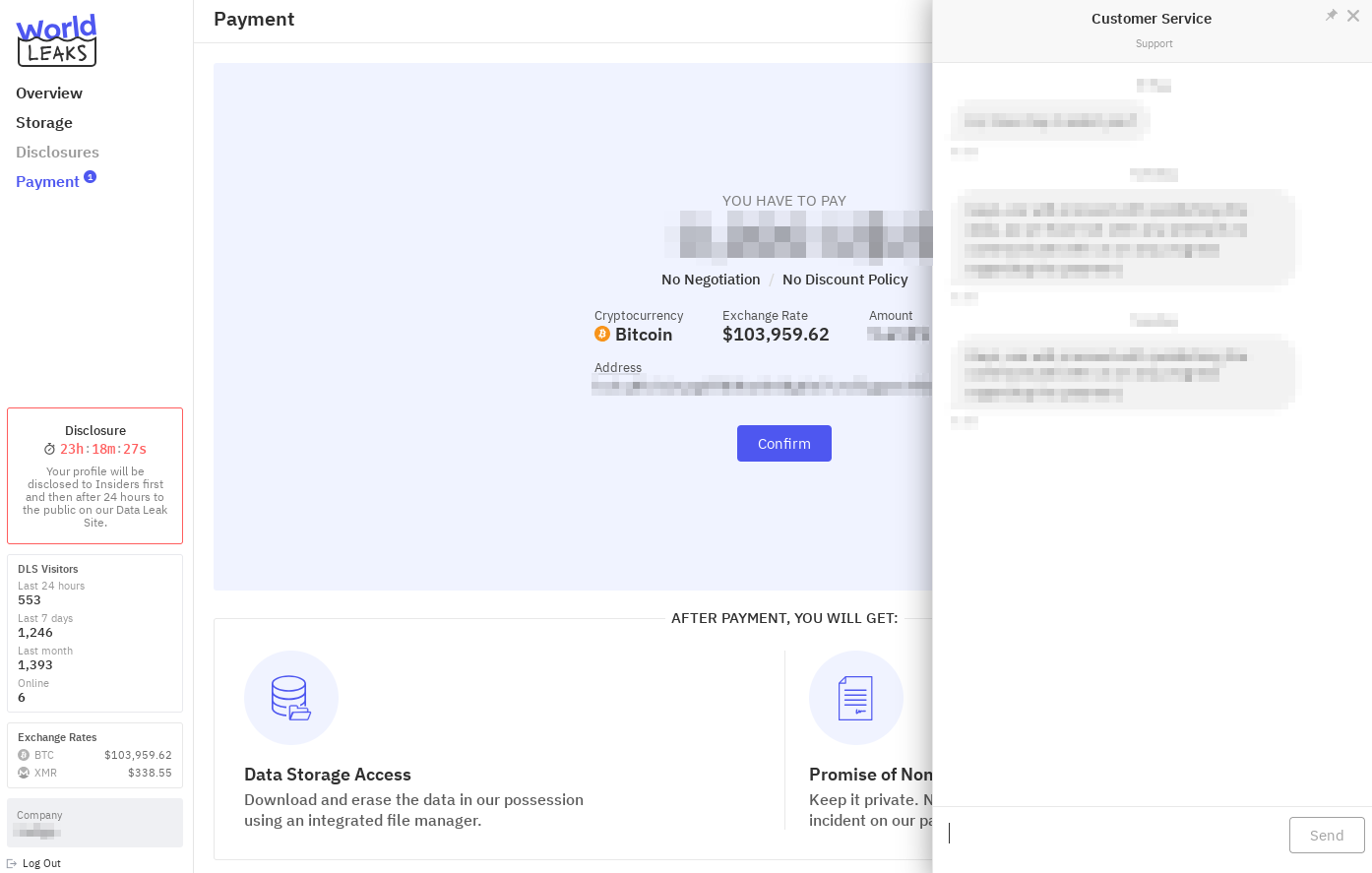
Finally, the interface also includes a countdown timer, indicating the deadline before the stolen data is published. The timer is designed to create additional psychological pressure: the ticking clock serves as a visual reminder that time is running out for the victim to comply with the ransom demand. The attackers amplify the sense of urgency by threatening full public disclosure unless payment is made before the deadline expires. This tactic is common in ransomware and extortion schemes: victims are given a limited window to respond, after which pressure intensifies. This pressure is not only through private threats but also by making the breach public, with all the reputational and legal consequences that come with it.
World Leaks’ Insider site
When registering for the Insider platform, users receive the onion URL of the platform along with their credentials. Initially, the account will have a "pending" status, presumably for manual approval, and it will not grant access to any information.
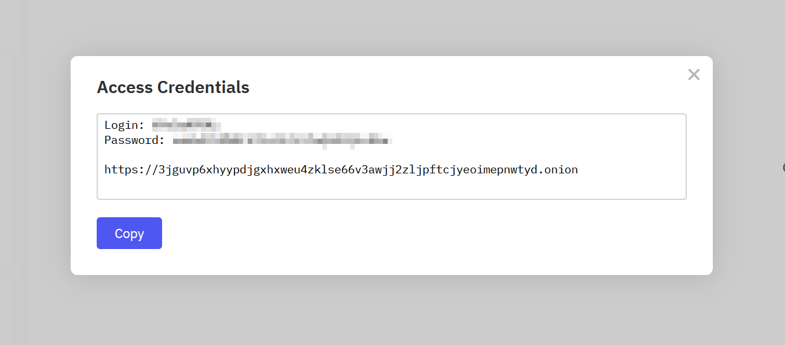
As stated in the News announcement and the Disclosure timer on the victim panel, being an Insider provides the advantage of accessing leaks 24 hours before the general public.
As previously mentioned, without an approved account, users do not have access to any information on the Insider platform.

Nevertheless, even with a pending account, users have access to the live chat on the Insider platform, theoretically to communicate with World Leaks' operators.
However, once the account has been approved, they are given access to the data of victims that are published on the Data Leak Site (DLS) but are not yet publicly accessible.
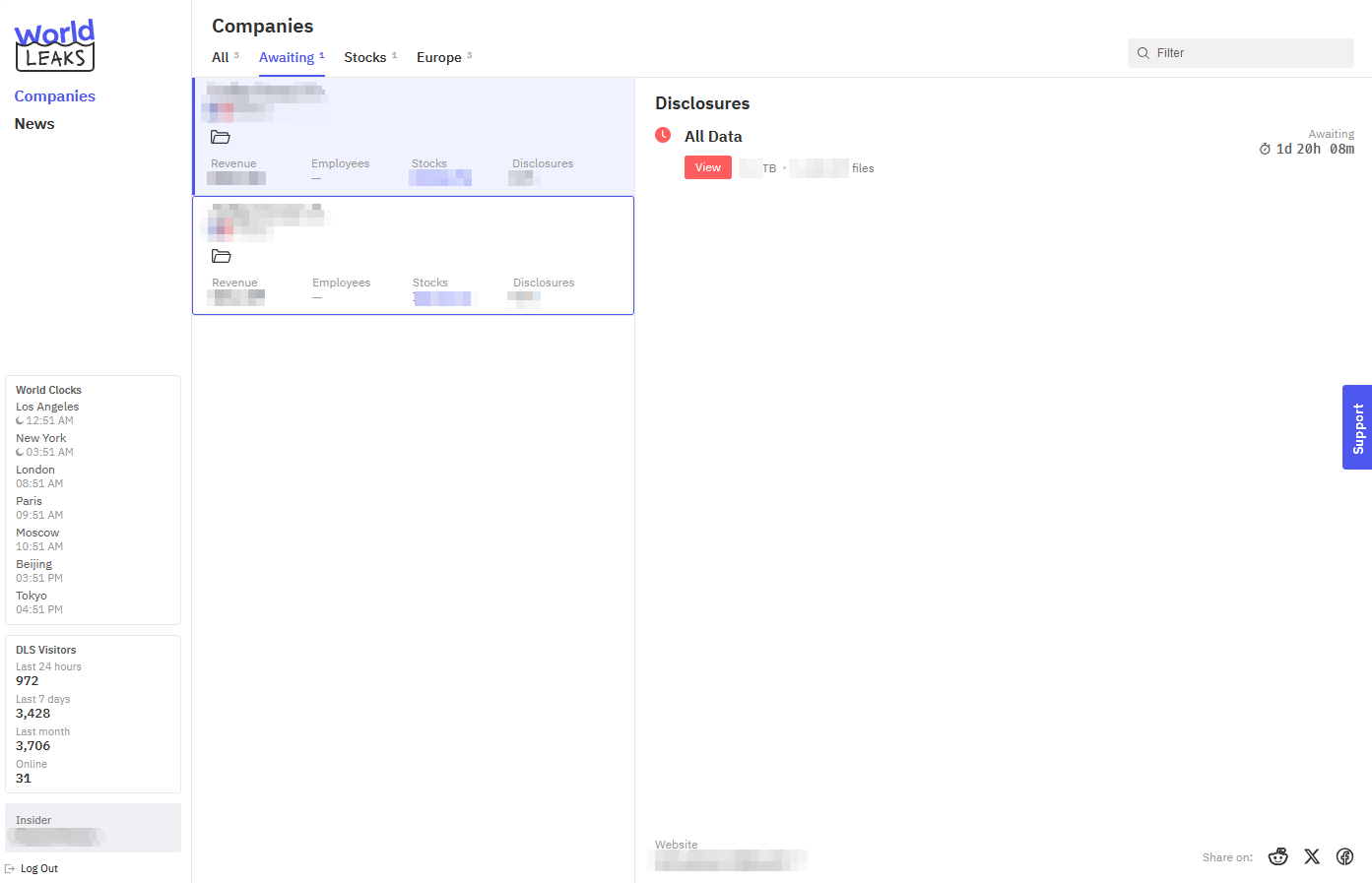
A Hazardous Beginning
World Leaks encountered some initial problems. According to Group-IB's report, after the platform was released in January 2025, the administrators discovered bugs in the World Leaks infrastructure and decided to pause the project until all issues had been resolved. Their first published victim was announced on April 29, 2025. The beginning was quite hazardous because they did not even respect their own deadline for publishing the victim's data. On April 29 at 15:48 UTC+2 (Paris Time), it was displayed for their first victim that the data would be published in 19 hours and 27 minutes, meaning it should have been published on April 30 at 12:03 UTC+2 (Paris Time). However, a check on April 29 at 17:16 UTC+2 (Paris Time) showed that the victim's data had already been published. This demonstrates a lack of professionalism from the World Leaks operators and a hazardous management of their leak publications.
Additionally, similar to Hunters International's Data Leak Site (DLS), World Leaks has experienced some downtime from time to time. Over the past month, Hunters International's DLS has been down multiple times and has encountered bugs, such as infinite loading when attempting to retrieve the list of a victim's leaked data. This instability in Hunters International's infrastructure could also occur in World Leaks. For now, World Leaks' infrastructure appears to be more stable than Hunters International's, but it could worsen with an increase in claimed victims and heightened activity on their platforms.
During our surveillance of World Leaks, we observed some fluctuations in the size of the claimed data leaks. Initially, it was displayed that one of the victims had suffered a 7TB data leak, but after a couple of days, this number dropped to 700GB; a few days later, it rose again to 1.5TB, and so on. The list of exfiltrated data was already present, and we are unsure what caused these fluctuations. This raises questions about the accuracy of the quantities of stolen data displayed and claimed by World Leaks on their site.
World Leaks’ affiliates
According to Group-IB's report, affiliates collaborating with World Leaks will be provided with a self-developed exfiltration tool designed to automate the data exfiltration process. The tool is purportedly easy to use and "100% fully undetectable." However, the use of this tool does not appear to be mandatory for affiliates.
While World Leaks claims to be a 100% extortion-only project, we can confirm that some of their claimed victims suffered ransomware deployment on their systems. We can state with high confidence that the ransomware group known as Secp0, which PRODAFT discussed in March, is collaborating with World Leaks. We will discuss Secp0 in more detail in another public report soon. In a recent blog post, Secp0 claimed that they are "testing a software solution designed to streamline the publication of large datasets." We believe with moderate confidence that Secp0 is referring to World Leaks.
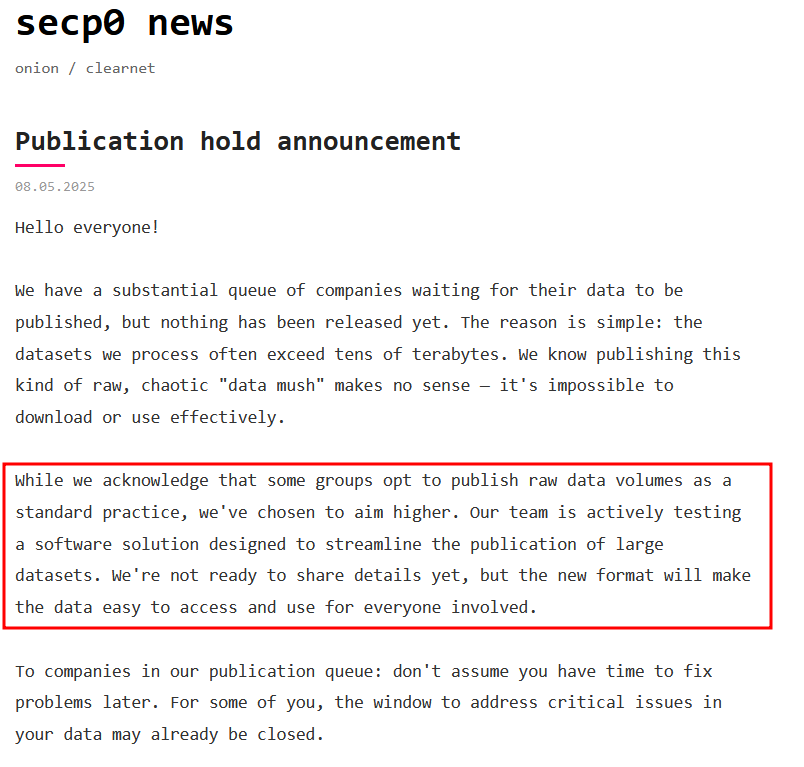
It will be interesting to see if the World Leaks project by the operators of Hunters International will attract other threat actors.
IoCs
| Indicators | Indicator type | Description |
|---|---|---|
| worldleaksartrjm3c6vasllvgacbi5u3mgzkluehrzhk2jz4taufuid[.]onion | onion address | World Leaks Data-Leak Site (DLS) |
| vw6vklsuotptwdbiwqfvd7y4b57wdbfm6ypxduzzgbt62snti6jm76yd[.]onion | onion address | World Leaks Victims Pannel |
| 3jguvp6xhyypdjgxhxweu4zklse66v3awjj2zljpftcjyeoimepnwtyd[.]onion | onion address | World Leaks Insiders Pannel |
