Introduction
In today's digital age, document fraud poses a considerable challenge, affecting both those who commit the fraud and the victims who suffer from it.
False documents can be used for a wide variety of illegal activities, such as providing proof of residence using false water and electricity bills, landing a new job using fake diplomas, opening bank accounts using fraudulent identification papers, and so on.
Contrary to popular belief, obtaining such documents doesn't require advanced artificial intelligence or a journey into the dark web. Many counterfeiting organizations provide their services on both the clear and deep web, often under our very eyes, making access to these falsified documents relatively easy. This article focuses on these two strata of the web.
Our research indicates that, much like threat actors, counterfeiters' infrastructures can be analyzed using various OSINT methodologies. We discovered that several websites and e-mail accounts often seemed to be linked to the same counterfeiter, allowing us to trace their identity.
This article explores the different facets of document fraud, how it operates and highlights the fact that the number of players behind these numerous online stores is relatively small.
The world of forgers
Context and reasons for using fakes
Obtaining a forged document has become easy and relatively accessible to many. Using artificial intelligence or tools such as Photoshop, documents can be generated or altered to yield realistic results, mimicking handwriting fonts, official stamps and signatures. For counterfeiters, the primary motivation is easy money. The production and sale of forged documents requires minimal initial investment, especially for exclusively digital versions, and can generate substantial revenues.
Buyers of forged documents have a variety of motivations, including engaging in illegal activities such as identity theft, industrial espionage or even terrorism, as well as using them in everyday life.
Falsified documents can also be used for clandestine operations carried out by state actors or private organizations. As demonstrated by the case of the North Korean “Fake IT workers”, malicious actors can make effective use of fraudulent documents. North Korean IT workers are using fake identities, fictitious LinkedIn profiles, forged documents and interview scripts to secure jobs at Western technology companies. These sophisticated strategies are designed to generate money to finance Pyongyang's nuclear program and carry out industrial espionage.
On a smaller scale, the purchase of false identity documents can be used to bypass KYC (Know Your Customer) identity verification procedures and facilitate banking or financial fraud.
The use of these forgeries is not always confined to criminal activities: some individuals use them to gain otherwise unattainable advantages, such as presenting a false diploma to secure a job. According to a 2024 survey by the French National Commission for Professional Certification (CNCP), some 20,000 fraudulent diplomas are produced in France every year.
"Ready-to-use kit" are sometimes available for sale, enabling prospective tenants to put together an appealing dossier without having the necessary resources. In this example, a "ready-to-use kit" of false documents to obtain a rental apartment:
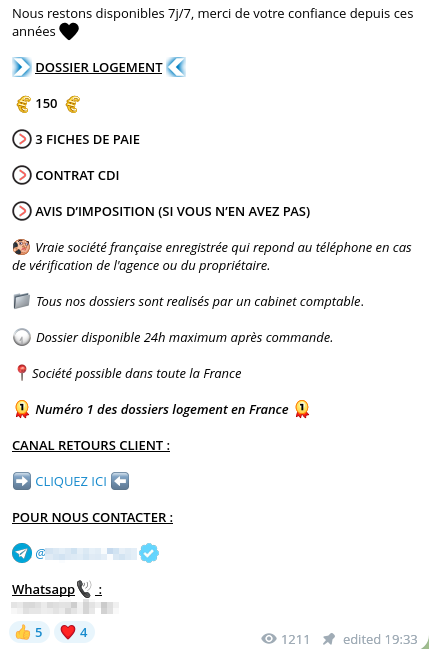
The use or fabrication of false documents carries severe legal penalties. In France, these offences are severely punished, with penalties that can increase depending on the circumstances:
Penalties for the user:
Use of false documents: Up to three years' imprisonment and a €45,000 fine.
Possession of false government documents: Up to two years' imprisonment and a €30,000 fine, and up to five years' imprisonment and a €75,000 fine if several false documents are held.
Use of false government documents to obtain a right or identity: up to five years' imprisonment and a €75,000 fine.
Forgery of a public or authentic document: up to ten years' imprisonment and a €150,000 fine.
Penalties for counterfeiters:
Forgery of a document normally issued by a public authority: up to five years' imprisonment and a €75,000 fine.
Forgery of a public or authentic document: up to ten years' imprisonment and a €150,000 fine, or up to fifteen years' imprisonment and a €225,000 fine if the person is a public official.
Falsification or fraudulent alteration of private documents (invoices, contracts): Up to three years' imprisonment and a €45,000 fine.
It is important to point out that attempts to commit these offences are subject to the same penalties.
Not-so-hidden platforms
Unexpectedly, the places where fraudulent documents are sold are not confined to obscure sites hosted on the dark web that only accept payments in Monero. On the contrary, the counterfeiters' ecosystem is vast and varied. We've explored the various strata of the web, to get an idea of how the sellers operate.
Dark Web
Sellers can be found on the dark web, where specialized marketplaces offer forged documents in exchange for cryptocurrencies. The descriptions are often sketchy, and the range of documents is limited.
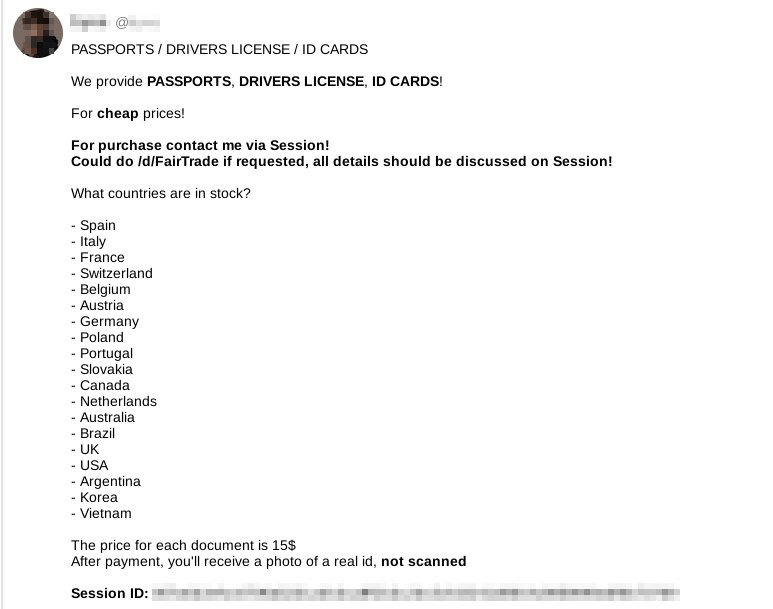
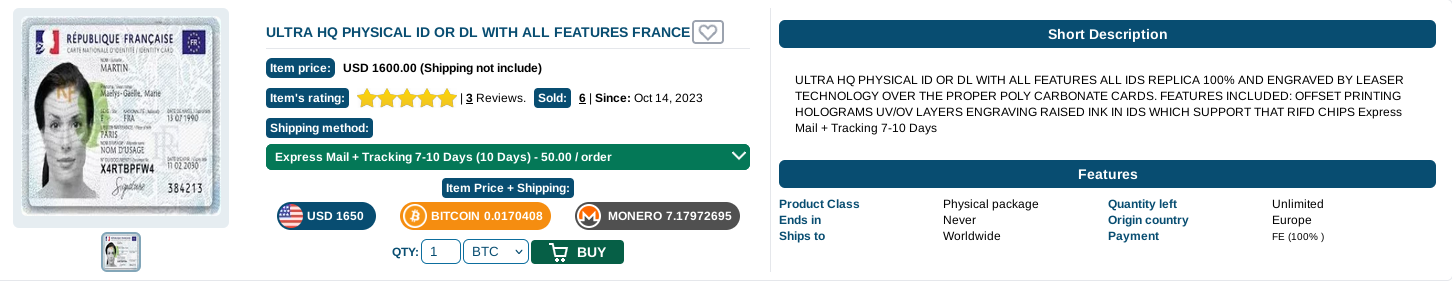
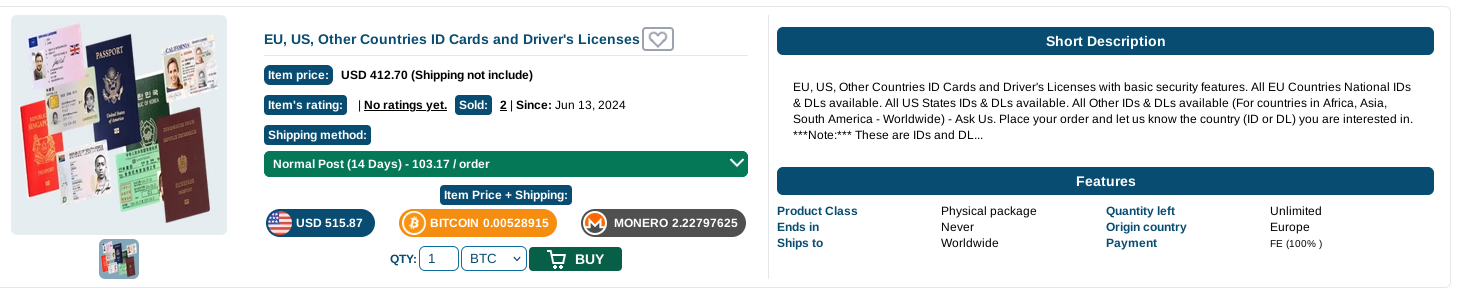
These items are handled like any other illegal items on these marketplaces. Since they have been the subject of many other articles, we won’t focus on them here.
Deep Web
A variety of specialized sellers can be found on less visible parts of the deep web, through messaging platforms or social networks.
A quick search using a few keywords on Snapchat reveals numerous accounts whose explicit names leave no doubt:
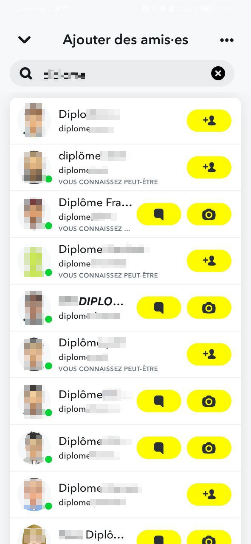
The same applies to other social networks like Facebook, Telegram, Snapchat, and WeChat, where dozens of sellers can be found using very simple keywords:
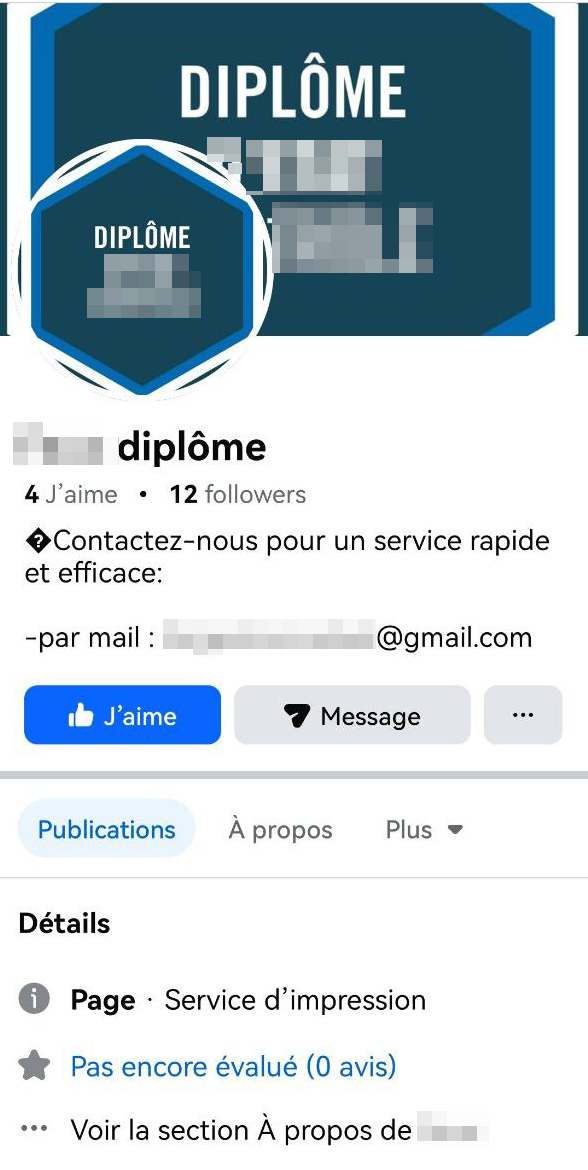
While some may be scams, others boast many satisfied customers and successfully deliver their products.
Clear Web
Our research has shown that many fraudulent documents are available for sale on websites present on the clear web, the visible part of the Internet, accessible with a basic Google search. The sites resemble typical e-commerce platforms: they are well-detailed, include photos, enable interaction with sellers for inquiries or more personalized products, and accept various payment methods.
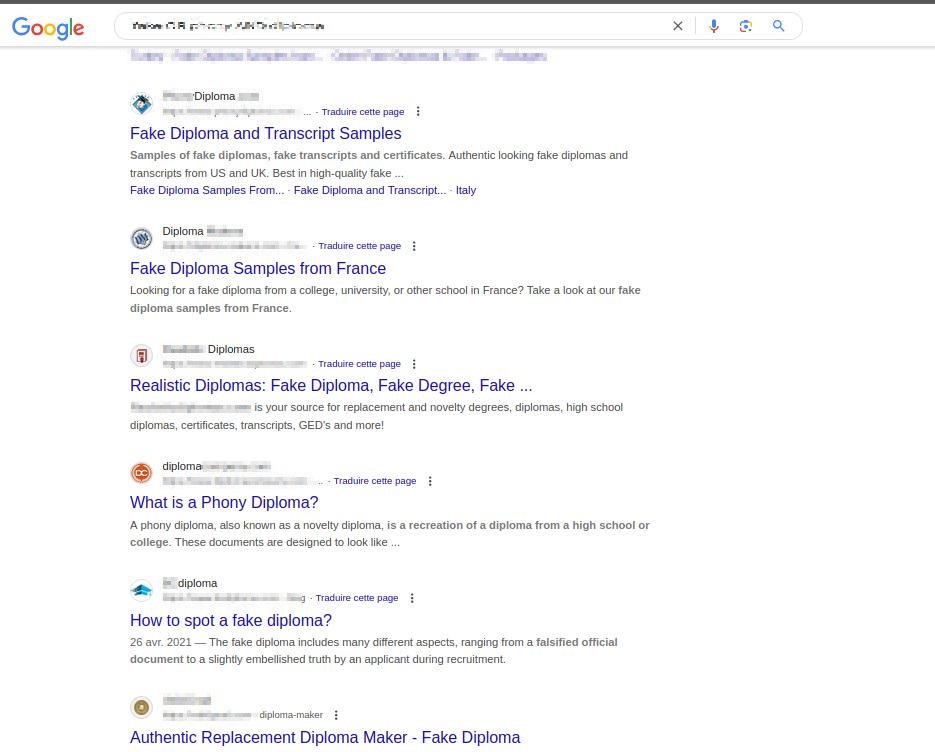
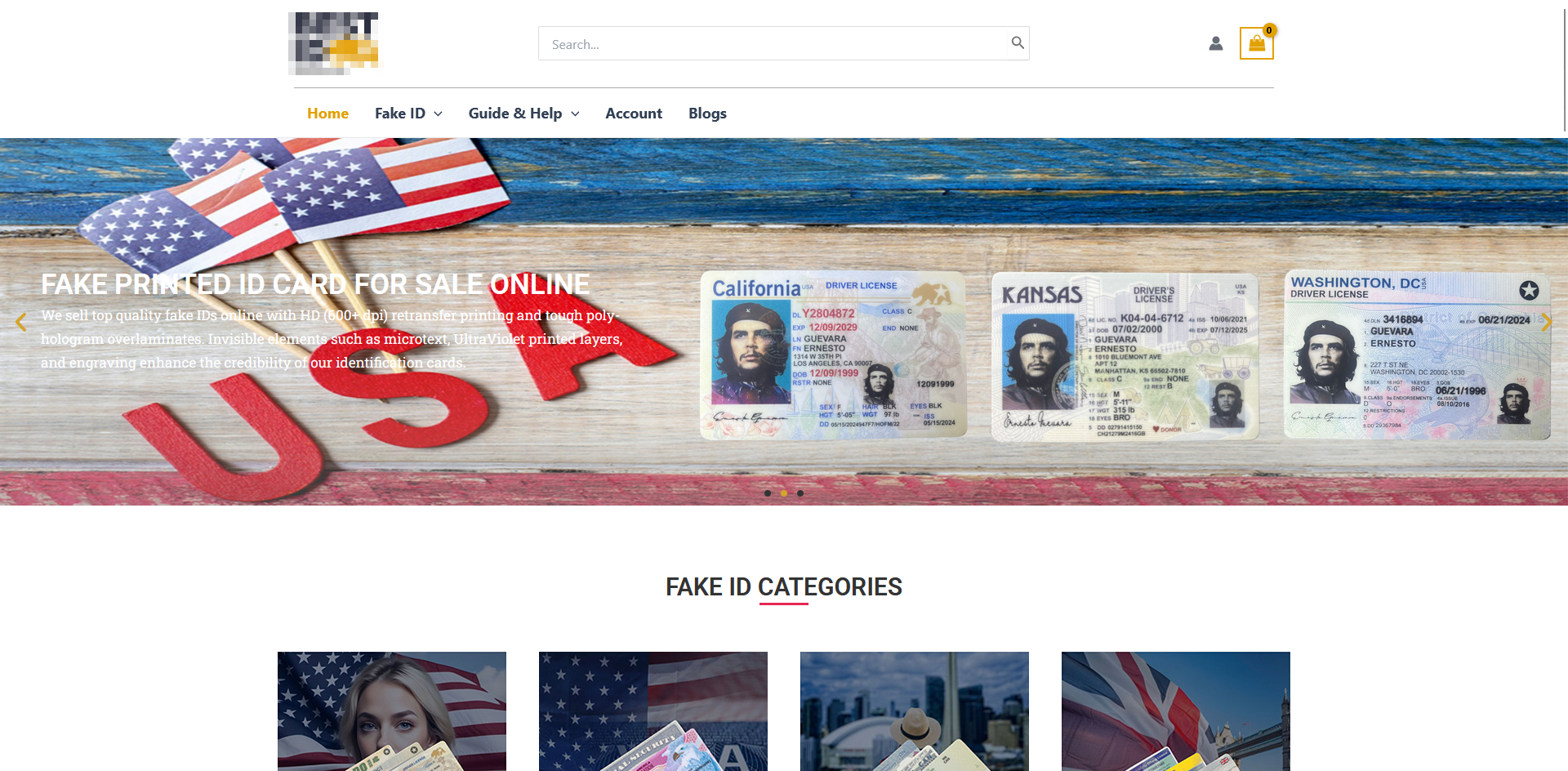
Payment methods
When it comes to payment methods, here too the choices may seem surprising from a security and anonymity point of view.

- The first category of payment methods includes traditional options like Western Union, bank transfers, Alipay and WeChat. The main drawback of these methods is that they involve intermediaries that are subject to strict regulations and monitoring systems designed to prevent fraud and money laundering. Additionally, registering for these services usually requires identity verification.
- Some platforms also accept cryptocurrencies. In some cases, payment is processed via an intermediary platform, such as Coinbase. Here, the issue is similar to the first category: the intermediary is bound by regulations and has access to the information of both parties, which means that anonymity is not maintained.
Most of the time, transactions are conducted directly from wallet to wallet, allowing you to obtain the seller's public address. This enables the tracing of previous transactions and provides insights into the seller's financial history. Although Bitcoin is often perceived as anonymous, it is actually pseudonymous; since each transaction is recorded on the blockchain, it is possible to trace the chain of exchanges and analyze financial flows. Blockchain analysis tools can identify connections between different addresses and, in some cases, reveal the identities of the parties involved. However, some sellers employ techniques such as mixers or more anonymous cryptocurrencies (Monero, Zcash) to reinforce the confidentiality of their transactions.
To illustrate the issue of using an unsuitable cryptocurrency for payments without additional protections, we'll analyze two examples encountered during our research. We came into contact with counterfeiters on Telegram and WeChat, posing as potential customers. To proceed with the settlements, they provided us with their TRC20 wallet addresses, allowing us to observe the financial activities of these criminals.
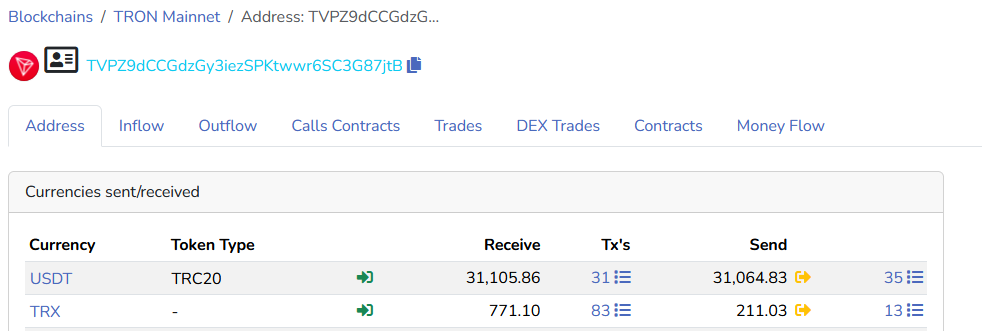
An analysis of the transactions issued from the first wallet (TVPZ9dCCGdzGy3iezSPKtwwr6SC3G87jtB), which appears to belong to a Chinese counterfeiter or group of counterfeiters, reveals that it would have received over $31,000 in USDT in 2024. This player, specializing in the sale of fake diplomas, offers a counterfeit Master's degree from a French school for $400, which makes it possible to roughly estimate the number of sales made that year.
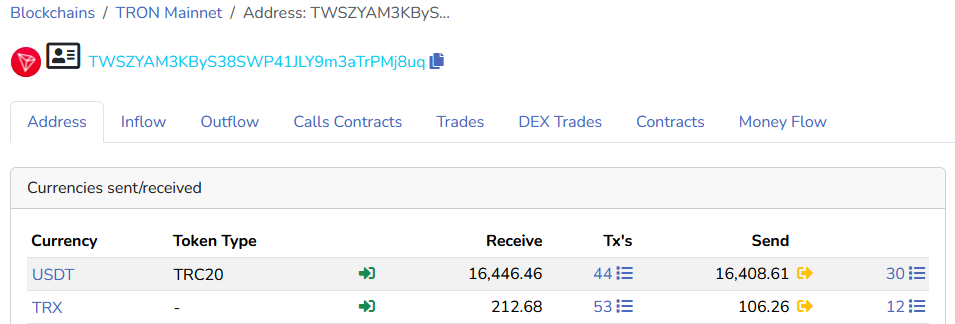
A second wallet (TWSZYAM3KByS38SWP41JLY9m3aTrPMj8uq), also linked to a Chinese counterfeiter or group of counterfeiters, reportedly received over $16,000 in USDT in 2024. The latter is said to sell a Master's degree from a French school for $550.
Marketing
To attract customers, counterfeiters on both the deep and clear web deploy a variety of dissemination strategies. We have noticed that some counterfeiters leave comments on various forums and websites, employing specific keywords and systematically including links to their website, Telegram channel or other communication platforms.
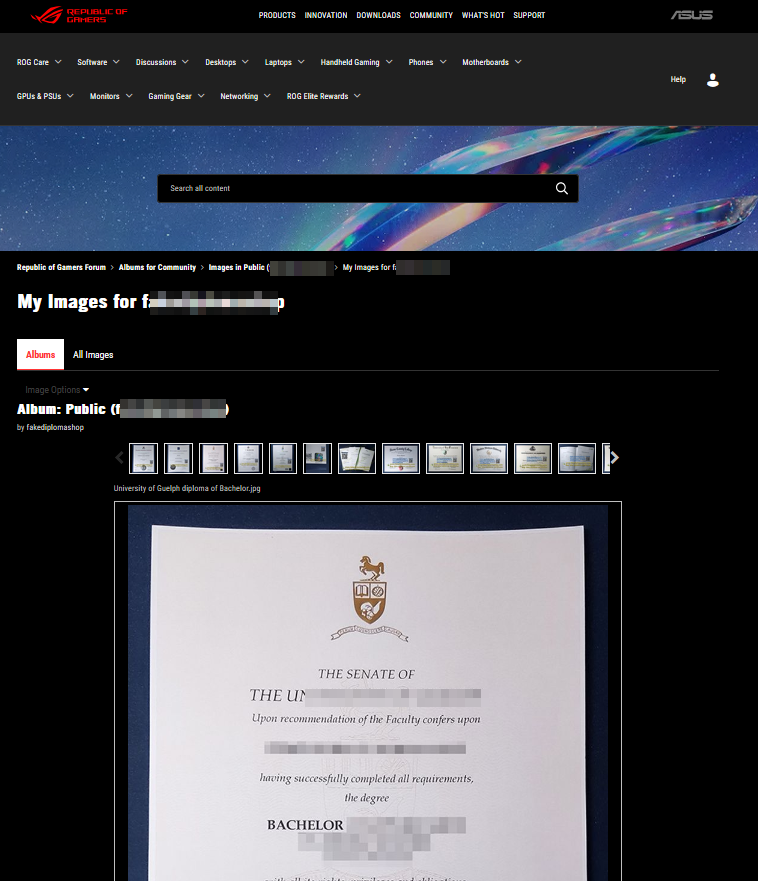
Other counterfeiters leverage document-sharing platforms like Issuu to advertise their services.
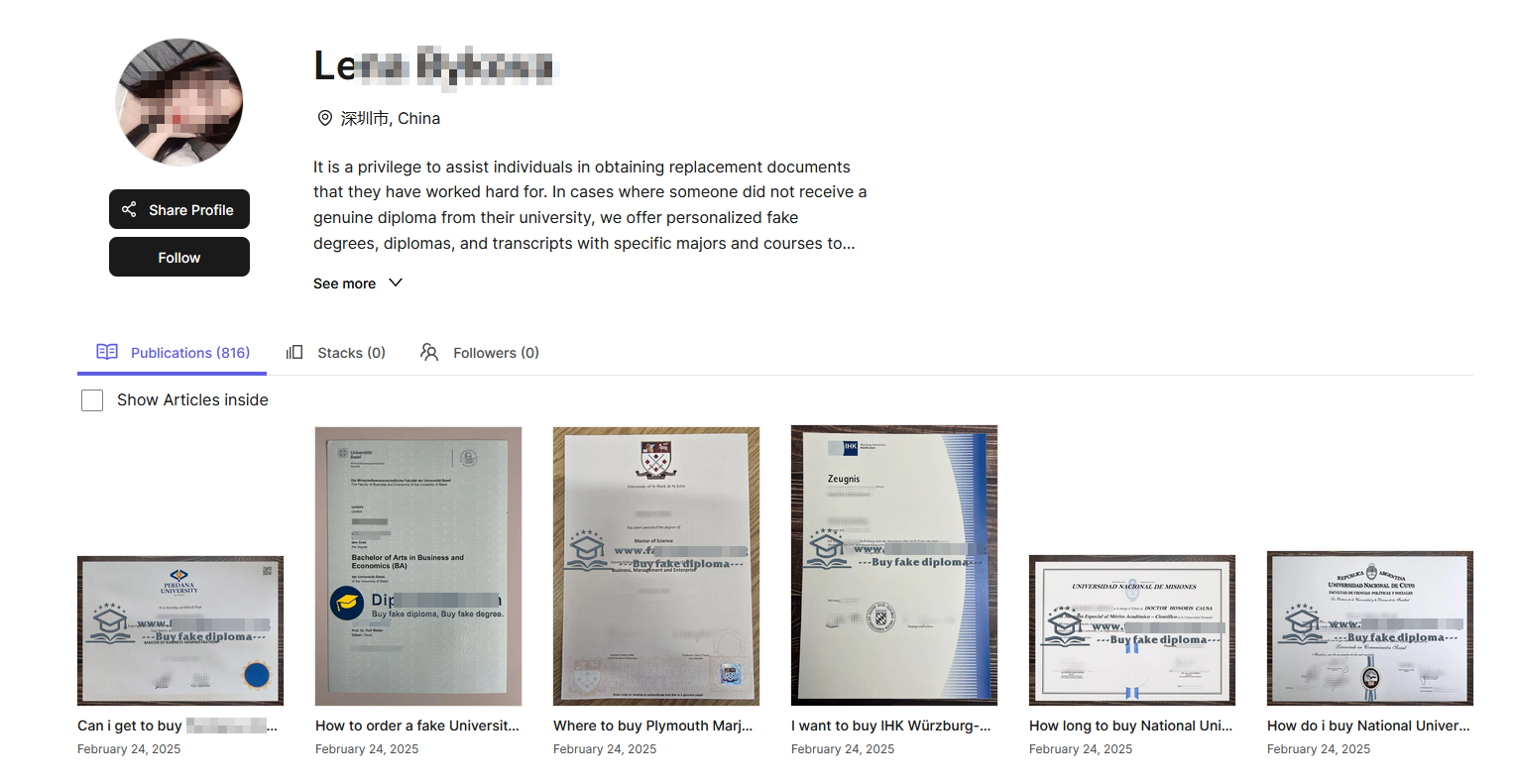
Some counterfeiters take it a step further by creating Google sites or free websites, populating them with hundreds of keywords and phrases that potential customers are likely to search for. These sites also include links to their sales platforms as well as contact methods such as email, Telegram, WeChat, etc.
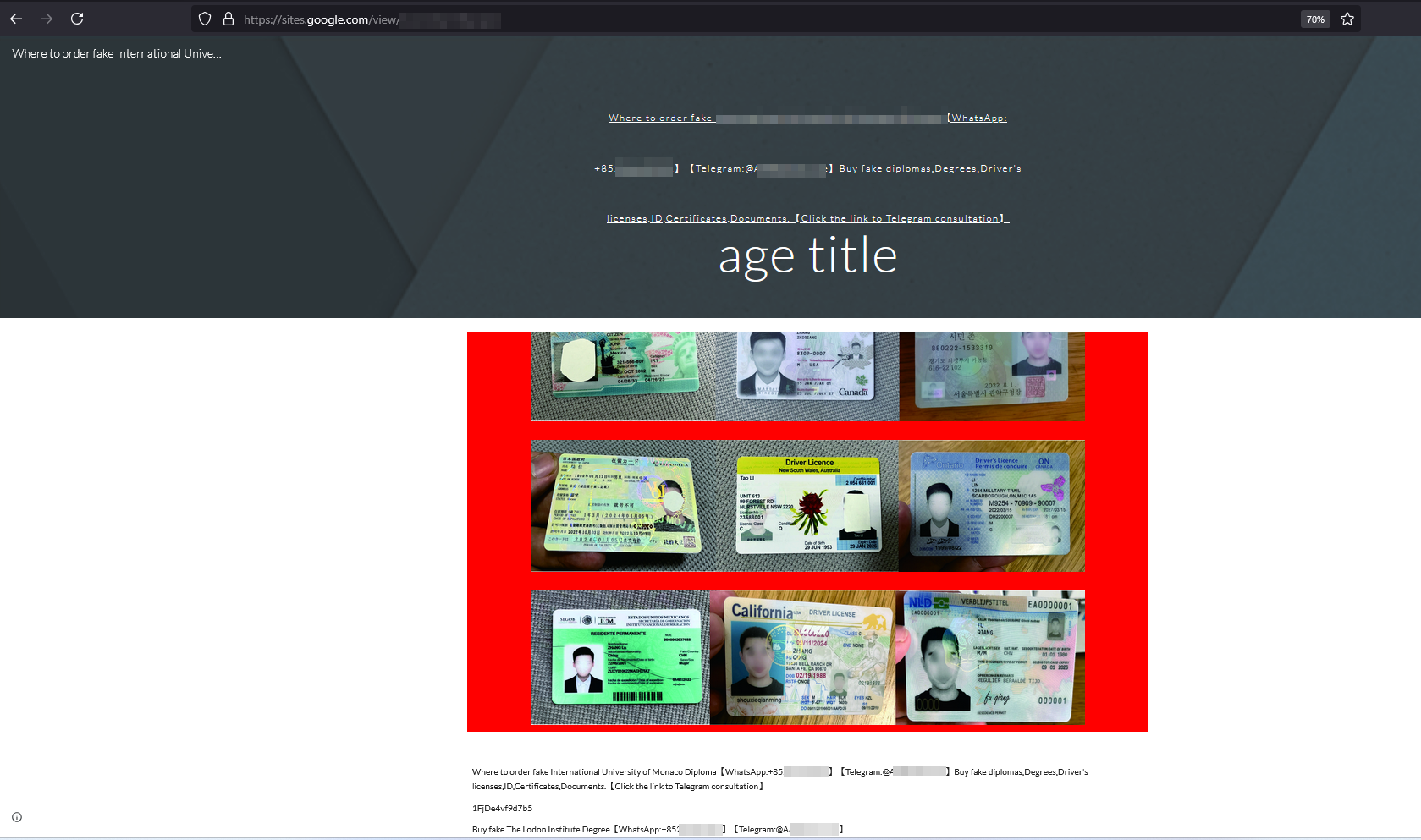
Similarly, some players simply use social networks to draw in customers and redirect them to the sales platform.

Investigation: a nebulous network of fake document websites
As mentioned above, there are numerous offers availaible on the Internet, which is why we've chosen to focus on them and examine them more closely.
As part of this investigation, we first explored various sites and social networks specializing in the sale of false documents, in order to analyze how they operate.
We quickly identified similarities among several sellers, indicating potential connections between them. We then set out to map these clusters and uncover the hidden links between them. In this section, we present two of them in detail.
General methodology
The general methodology used to identify other sites within the same cluster is based on a systematic, iterative process.
In each example, we will begin with a different site, which will serve as the basis for our analysis. All singular information will be extracted, and each piece will become a pivot point for discovering new sites.
To discover and map these networks, several pivot techniques were used:
Search for reuse of exact terms: identification of characteristic elements of sites such as e-mail addresses, telephone numbers, domain names, postal addresses, etc.;
Analysis of visual resources: identification of sites sharing the same images, whether logos, watermarks or product photos;
Study of textual similarities: search for sites using the same marketing formulations or general terms and conditions;
Exploitation of watermarks: extraction and search for store names visible on images of documents offered for sale;
Investigation of commercial entities: verification of companies (real or fictitious) associated with identified sites, by cross-checking information;
Analysis of hosting infrastructures: search for relevant sub-domains on IP addresses hosting counterfeiters' sites, using DNS records;
Exploration of social networks: examination of subscribers, subscriptions and interactions of accounts linked to these platforms;
Tracking of financial flows: identification of sites sharing the same payment recipients, revealing direct connections between different entities.
This modus operandi allows for the detection and linking of counterfeiters' sites, even when they attempt to mask their connections through the use of different hosts, distant domain names, or inconsistent information.
By applying this methodology, it becomes possible to reveal organized networks, often structured around the same operator or criminal group. Links are meticulously validated, by cross-referencing sufficient commonalities.
"Chinese" cluster
The investigation into this cluster started with the document-sharing platform Issuu. Numerous accounts on this platform promote sites that sell fake documents, including some that specialize in counterfeit diplomas. We became interested in one of these accounts, which was posing as a Chinese user living in Shenzhen, China. On this account, we found two Chinese phone numbers, one linked to a WhatsApp account and the other to a WeChat account, along with an email address and the URL of the site selling fake diplomas.
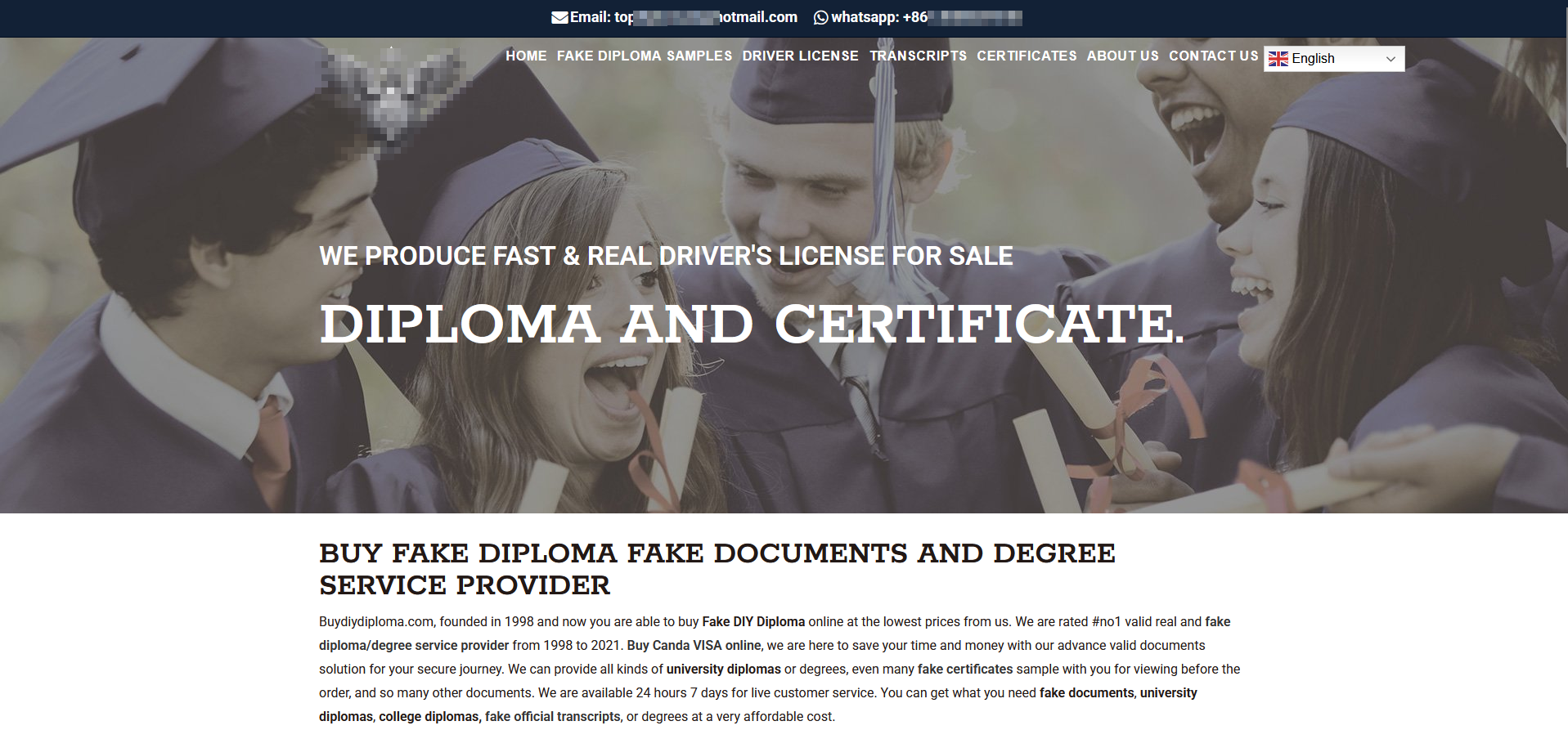
The site offers various communication channels to enable customers to get in touch with the counterfeiter(s). These include:
A Chinese phone number starting with +86 to contact them on WhatsApp;
A WeChat pseudonym;
An e-mail address;
A Hong Kong phone number starting with +852 to contact them via Telegram.
The website also maintained a presence on social networks, including Twitter/X, Pinterest, Facebook and YouTube. However, the Twitter/X account no longer exists, as do the Facebook and Pinterest accounts. The YouTube account, meanwhile, has been banned. Thanks to Wayback Machine, it's now possible to verify whether these accounts ever existed.
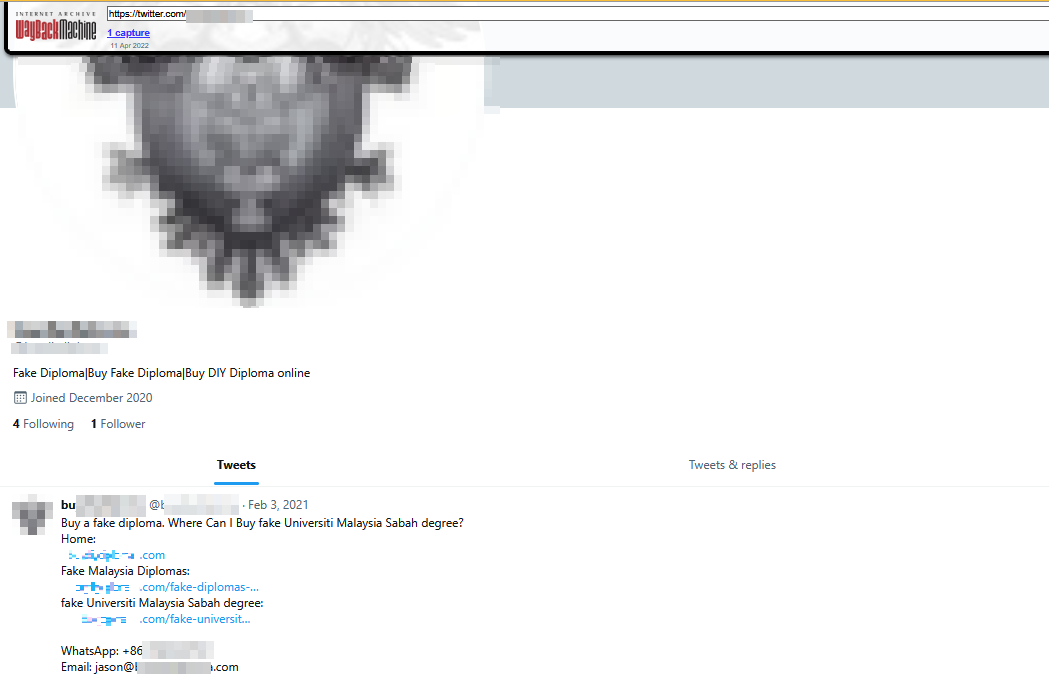
To avoid promoting the fraudulent site, we will refer to it as “FakeDocsHub”.
To maintain a high ranking in Google search results, FakeDocsHub features a blog with various articles always centered on the same topics and contain repetitive texts.
Several languages are available: English, Arabic, Traditional Chinese, Dutch, French, German and Hindi. In traditional Chinese, the Taiwanese flag is displayed.
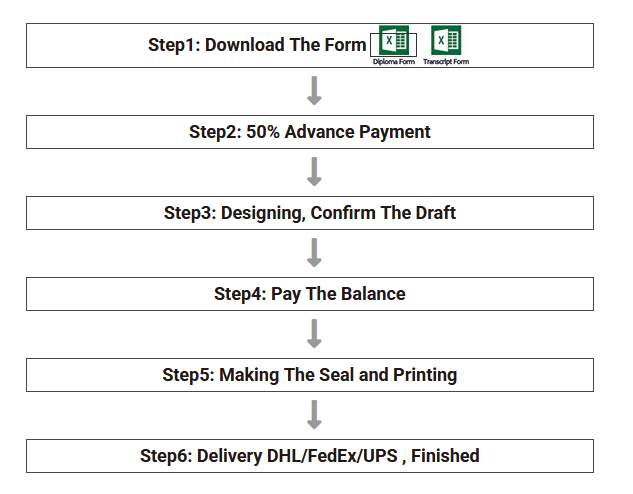
The process for ordering a fraudulent document on these sites is relatively straightforward: download, fill in and send an Excel form. A payment of 50% of the total price is then required. Once this payment has been made, the counterfeiters produce the document and provide a sample of the finished product for approval, after which they request the remaining payment. The forgers then finalize the document, print it and ship it to the specified address.
The Excel form's metadata is written in simplified Chinese and includes references to China.
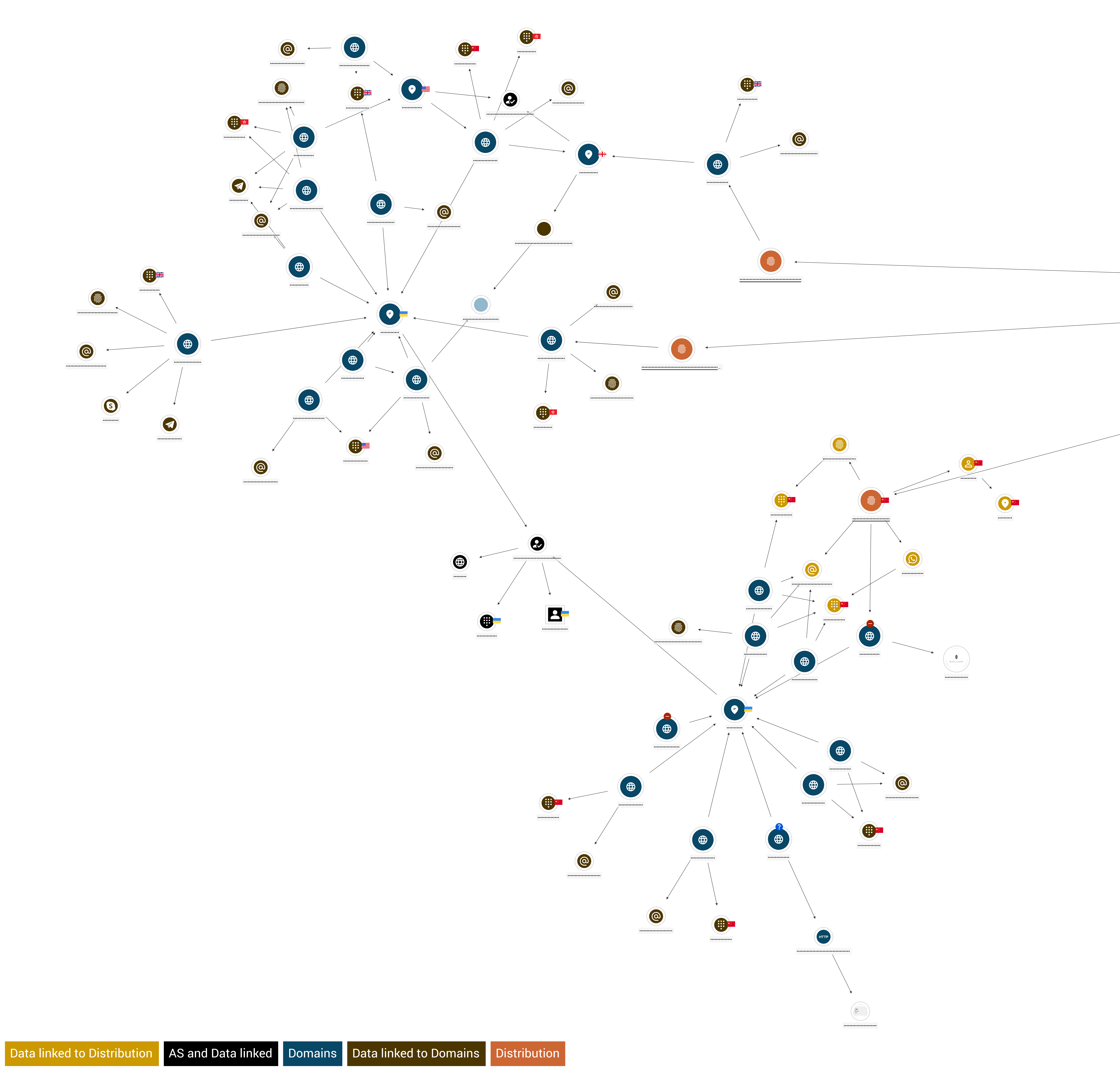
From the IP address of this site, and using various pivot methods, we discovered a more complex infrastructure. In total, we identified:
22 domain names;
4 IP addresses;
2 AS (Autonomous Systems);
13 e-mail addresses;
6 Chinese telephone numbers;
3 Hong Kong telephone numbers;
2 British telephone numbers;
1 American telephone number;
Several Telegram, WhatsApp and WeChat accounts.
It should be noted that one of the two ASes has hosted fraudsters' infrastructures in the past, including C2 (Command and Control) and malware like RAT Remcos, according to ThreatFox.
This cluster of websites specializing in fraudulent documents is mainly focused on fake diplomas, although some sites also offer fake papers such as driving licenses or ID cards. To reach their clientele, we have identified three distribution vectors:
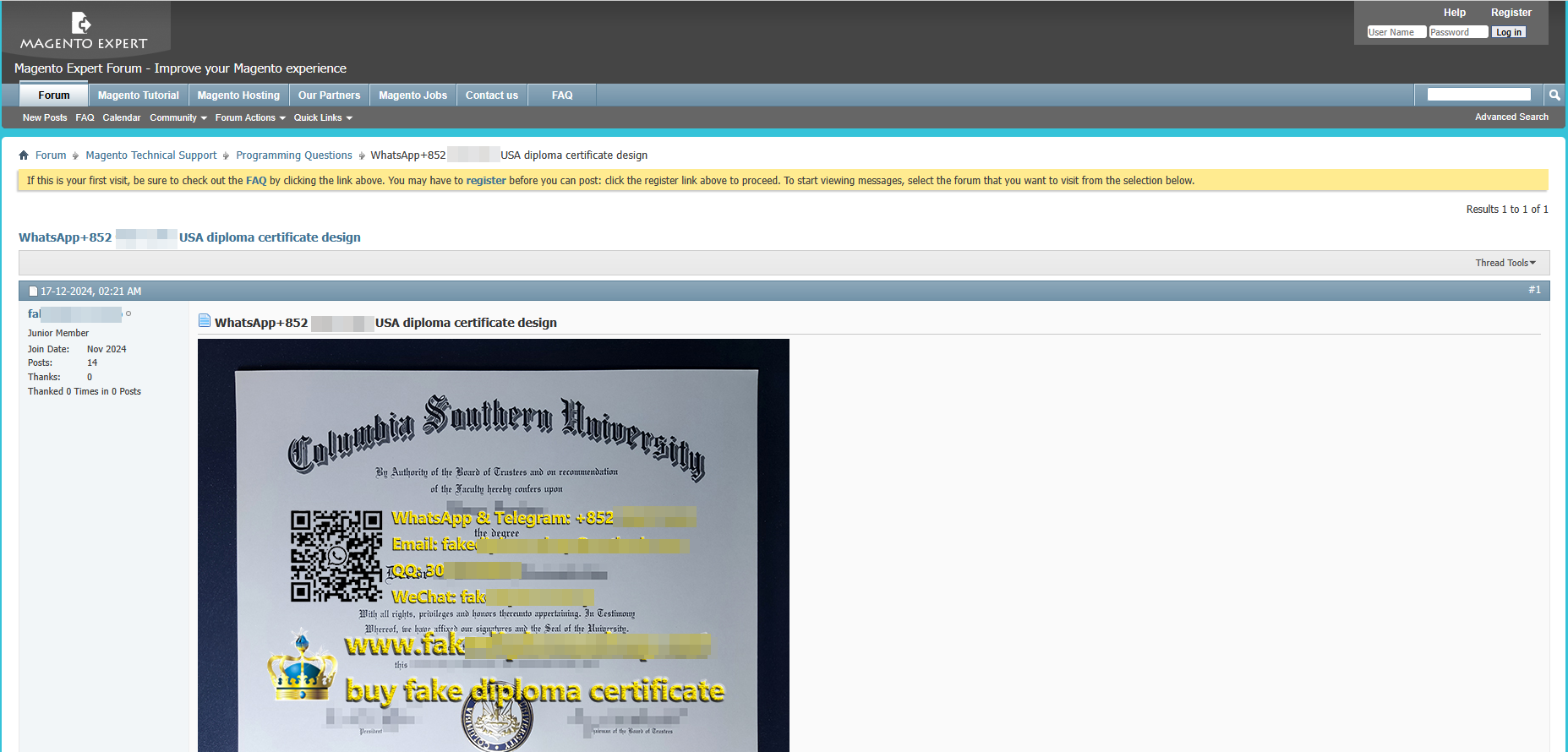
On Issuu, through numerous posts containing keywords related to fake diplomas;
On forums, through the publication of messages containing keywords related to fake diplomas and links to websites;
On social networks.
In particular, we've seen posts on the Magento Expert forum, a self-help forum for Adobe Commerce's B2B enterprise solution (Magento), as well as on the official forum of OnePlus, the Chinese phone manufacturer.

Several elements point to a direct link with China:
The use of Chinese and Hong Kong telephone numbers.
The use of WeChat for communication, an application widely used in China.

- The use of Alipay for payments, a Chinese platform.

- Errors in Chinese on some web pages.

- The integration of 51LA on certain sites, a Chinese equivalent of Google Ads.
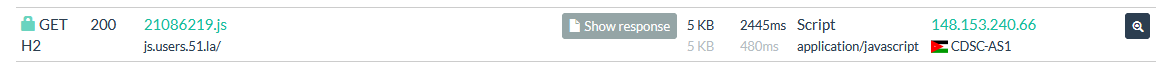
- Simplified Chinese metadata in Excel documents.
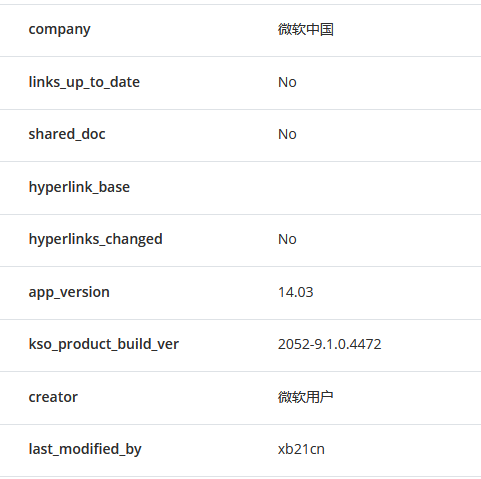
These clues suggest that the forgers behind this cluster may be operating from China. However, without more substantial evidence, this hypothesis cannot be definitively confirmed.
"US" cluster
For this cluster, we started with a site found through standard Google search, selecting the first result. The site, which specializes in the sale of fake diplomas, exhibits the typical characteristics of such platforms, along with several distinctive features:
An American telephone number;
A Google Maps page with reviews;
A postal address;
Three e-mail addresses associated with the domain name (support, sales, graphic designer);
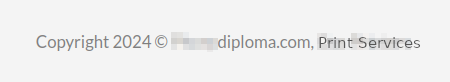
A company name distinct from the domain name, visible in the footer and in the privacy policy. To keep the sites anonymous, we have renamed it "Print Services".
The first phase involved analyzing the domain name using several specialized search engines. This initial investigation quickly uncovered another site selling fake diplomas, as well as two platforms dedicated to ranking sellers of fraudulent documents. These platforms publish evaluations and tests, making it easier to identify new players in this market.
We then applied the same methodology to each new item discovered, systematically repeating the analysis to broaden our field of investigation. We also found several companies, including a real one, around which the various sites revolve. From the latter, we were able to trace the identity of the counterfeiter, his various personal social networks, his address, and more.
Using these methods, we identified the following elements:
14 domain names;
9 e-mail addresses;
4 AS (Autonomous Systems);
2 companies;
1 Coinbase account;
1 Turkish telephone number;
1 Hong Kong telephone number;
9 American telephone numbers;
1 Twitter account;
3 Instagram accounts;
1 American postal address;
1 Hong Kong postal address;
The identity of one of the people behind the cluster, as well as his personal social networks and address.
To enhance its visibility, this cluster also uses a publication on Issuu, and maintains several more or less active social networks. A few Facebook accounts are shared among all the sites, despite their different names, featuring several hundred subscribers but only a limited number of publications. Less traditional social networks, such as Pinterest, are also used.
Less traditional social networks, such as Pinterest, are also used.
What's more, the fictitious company name present on nearly all the sites has a well-crafted Google Reviews page, boasting an impressive rating of 4.8 stars from 64 reviews.

However, upon examining the various reviews in detail, some of them (glowing with a 5-star rating) appear to be fake. A reverse image search of the profile pictures from accounts featuring visible faces reveals that almost all the faces actually belong to pornographic actresses.
The most interesting marketing aspect is one of the two counterfeiters' ranking and review sites discussed above. In fact, the DNS record shows the name of the company that registered it, which is none other than the same company that registered several other sites in this cluster. And of course, the sites featured and highly rated in the ranking also belong to this cluster.
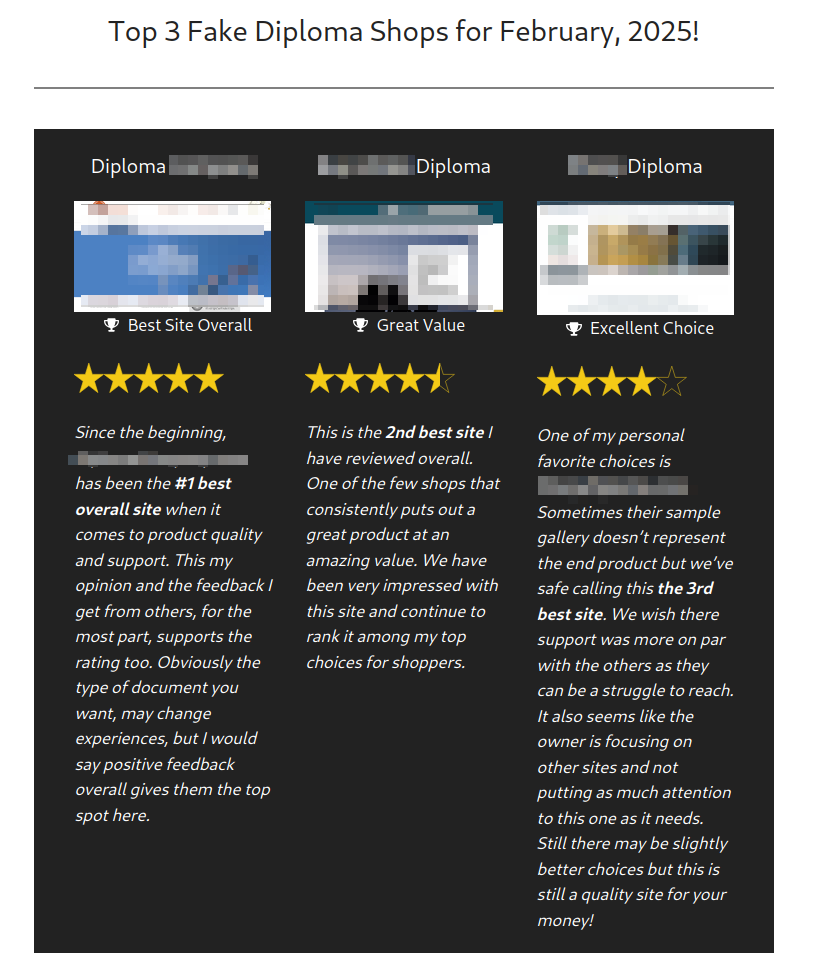
The other sites presented and not part of the cluster are judged more harshly:
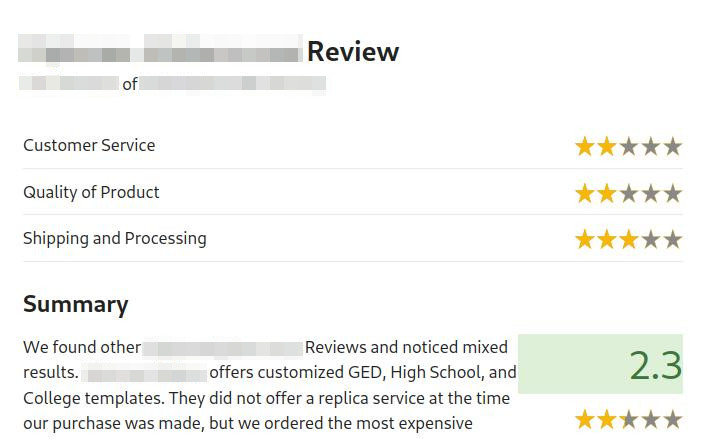
Going back in time with the Wayback Machine, the ranking varies. We come back to other sites identified in the cluster, some of which are no longer active but were also captured by the Wayback Machine.
Various elements indicate that the cluster may have American origins:
The majority of diplomas offered are from American schools;
The majority of telephone numbers are located in the USA;
Five sites have a U.S. postal address;
Several domain names are registered by a Virginia-based company;
Opening hours and delivery times correspond to American holidays and office hours. Some are specific to the USA, such as July 4th:
"Our support and production departments are open from 9am to 4pm EST"
- "Our offices are closed weekday nights and weekends. We are also off on major US holidays including New Years, July 4th, Memorial Day, Thanksgiving and Christmas."
- "Support is very limited on limited Christmas Eve & Thanksgiving Eve and the Friday after Thanksgiving."
- "LIVE CHAT and TEXT customer support from 9:00am to 4:00 pm Monday - Friday Eastern Time. Email us anytime!"
"This depends on when we receive your order and payment. Times do not include Weekends or Holidays, though we can have a digital copy to you within one business day, and we offer UPS shipping, with tracking, all across the US and Abroad."
The real company behind the sites is located in the USA, in an identified state;
The counterfeiter whose identity was found also resides in this state, in the USA;
Another particular point to highlight is the consistent presence of the page “Restrictions & Limitations - What We Don't Do” across the sites in this cluster, which includes the following paragraph: “Even being strictly for novelty purposes, as print shop we choose not to print any sort of law or medical documents. This applies whether the document is for a graduate or undergraduate request. We will also not print any request, if we believe you plan to use our services in a way that may bring a threat or harm to others. In this circumstance services will be refused, documents denied, etc.”. This recurring mention could reflect either an attempt by counterfeiters to present an ethical facade, or a strategy aimed at protecting themselves legally by complying with certain stricter regulations.
Possible links between these two clusters
During our investigation, we were unable to find any formal proof that the two clusters formed a single entity. Nevertheless, several elements seem to link them:
- A large proportion of the sites in the “US” cluster display the words “Copyright 2024 Site_Name, Print Services” in the footer. One of the sites in the “China” cluster has a similar one.


- As mentioned earlier, several sites in the Chinese cluster require users to fill out and submit an Excel document to order a fake diploma or transcript. A site in the US cluster also uses a similar process. To highlight potential connections, we compared the different metadata of these 4 documents.
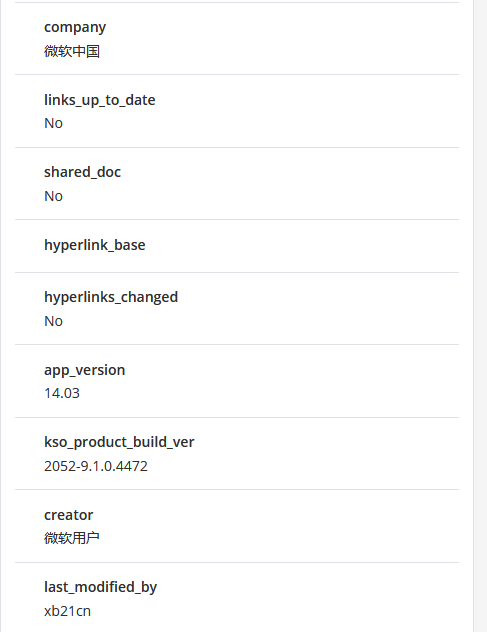
The following table summarizes the metadata for the statement order document and diploma order document for the Chinese cluster, and the same documents for the US cluster:
| Transcript - "Chinese" Cluster | Transcript - "US" Cluster | Diploma - "Chinese" Cluster | Diploma - "US" Cluster | |
|---|---|---|---|---|
| Heading Pairs | 工作表, 3 (Worksheets, 3) | |||
| Creator | Administrator | Administrator | 微软用户 ( Microsoft user) | 微软用户 ( Microsoft user) |
| Last Modified By | xb21cn | 忍者 (Ninja) | xb21cn | 忍者 (Ninja) |
| Create Date | 2016:02:12 15:20:00Z | 2016:02:12 15:20:00Z | 2013:05:16 15:11:57Z | 2013:05:16 15:11:00Z |
| Modify Date | 2020:12:02 08:28:05Z | 2024:04:29 16:30:14Z | 2020:12:02 08:27:43Z | 2024:04:29 16:29:40Z |
| KSOProductBuildVer | 2052-10.1.0.7224 | 2052-12.1.0.16729 | 2052-9.1.0.4472 | 2052-12.1.0.16729 |
| Company | 微软中国 (Microsoft China) | 微软中国 (Microsoft China) |
Documents of the same type in the Chinese cluster share the same creator, create date and company fields as those in the US cluster.
However, the fields heading pairs, last modified by, modify date and KSOProductBuildVer differ between the two clusters.
It seems likely that the documents in the US cluster were likely derived from those in the Chinese cluster, and subsequently modified.
Conclusions
To keep this article concise, we have opted to present only two clusters, which consist of about thirty sites. In just a few weeks of research, we managed to analyze over a hundred sites, divided into several clusters of varying sizes, on the clear web alone.
This digital landscape is evolving at a rapid pace: during the period under observation, some sites have vanished while others have emerged, illustrating the fluid and adaptable nature of this ecosystem, which complicates efforts to fully comprehend it. In fact, a more thorough investigation is likely to uncover connections between these clusters that are currently hidden.
Grouping sites into clusters makes it clear that this sprawling ecosystem is actually managed by a small number of individuals. This consolidation simplifies legal action by allowing authorities to target the responsible parties directly, especially as we've already been able to identify some of them ourselves. What's more, this strategy enables them to promote themselves, as demonstrated with the fake counterfeiters' ranking site controlled by the same individual managing the listed sites. It also boosts Search Engine Optimization (SEO) by establishing connections between the various platforms.
Recommendations
The fight against forged documents calls for a number of enhanced verification and authentication measures. For passports, registration in international databases, combined with security features that are difficult to reproduce but easy to verify, such as watermarks and holograms, help to reduce forgery. In the insurance sector and for other invoices, incorporating a QR code that links to a webpage with the certificate allows for instant verification of authenticity.
Regarding diplomas, France is gradually establishing an official platform enabling employers and institutions to verify the validity of diplomas online. For the time being, this verification is limited to about ten state diplomas, but it is expected to expand over time. In addition, some schools are experimenting with the use of blockchain to secure certificates and guarantee their immutability.
Although these initiatives aim to centralize and authenticate documents, their effectiveness still depends on their widespread adoption and systematic application.
